iPhone Virus Warning: How to Get Rid of Fake Apple Security Alerts
What to know.
- Don't tap on fake iPhone virus links or pop-ups; block pop-ups on Safari.
- To block the link or pop-up, tap the tabs icon, then swipe or tap the X icon to close the window. Toggle on Airplane mode, and clear your cookies & data.
- Fraudulent virus warnings and phishing sites are common scams.
It can be alarming when you're browsing a website, and a pop-up appears warning you of an iPhone virus. Fake Apple virus warnings, messages, and Apple security alerts are scams designed to get you to call or tap on a link. Fake Apple virus warnings are dangerous, so follow the steps below on how to safely stop these scams by turning on pop-up blocker settings.
How to Get Rid of Fake iPhone Virus Warnings
If you get a virus warning in a pop-up that says something like "Apple Security Warning on iPhone, Virus Detected," the first thing to remember is that there is no such thing as a real Apple security alert on an iPhone or iPad. Don't tap on it or call any numbers listed on the fake alert; don't even tap on the pop-up to close it! Some scam alerts seem to have an X or Close option that only resembles a close button but will actually direct you to the phishing site. Instead, follow the steps below:

Now you can open Safari again; at this point, Apple virus scams shouldn't be appearing anymore. If you didn't click on or interact with the fake virus warning, all should be well with your iPhone. If you're curious to learn more about iPhone security, we've also published other articles about iPhone viruses and security, including Step Up Your Security: 7 Ways to Up Your Game , and How to Block Caller ID on iPhone & Make Private Calls .
- How do I know if my virus warning is real? Your iPhone and iPad don't perform malware scans, so any pop-up warning you get is fake, every single one of them.
- How do I install Apple security updates to make my iPhone and iPad less vulnerable to malware, including viruses? The latest iOS update for your iPhone and the latest iPadOS update will improve your device's security, but you'll still need to follow the steps above to safely get rid of fake Apple virus warnings and security alerts.
- What is iOS Rapid Security Response; will it protect my iPhone from fake Apple security alerts? According to Apple, Rapid Security Responses "deliver important security improvements between software updates." These updates can't help you if you click on fake Apple security warnings.
Author Details

Leanne Hays
Leanne Hays has over a dozen years of experience writing for online publications. As a Feature Writer for iPhone Life, she has authored hundreds of how-to, Apple news, and gear review articles, as well as a comprehensive Photos App guide. Leanne holds degrees in education and science and loves troubleshooting and repair. This combination makes her a perfect fit as manager of our Ask an Expert service, which helps iPhone Life Insiders with Apple hardware and software issues. In off-work hours, Leanne is a mother of two, homesteader, audiobook fanatic, musician, and learning enthusiast.

Featured Products

Most Popular
How to Tell If Someone Blocked Your Number on iPhone
10 Simple Tips To Fix iPhone Battery Drain
How to Schedule a Text Message on iPhone
iPhone Alarm Volume Low? How to Make an iPhone Alarm Louder

How to Tell If a Dead iPhone Is Charging

How To Put Two Pictures Together on iPhone

How to Fix Apple Watch ECG Not Working

How to Hide an App on Your iPhone

How To Turn Off Flashlight on iPhone (Without Swiping Up!)
Can iPhones Get Viruses? How to Detect & Remove Malware (iOS 17)
How to Get Automatic Birthday Reminders on iPhone

How to Transfer Call from Apple Watch to iPhone
Featured articles, why is my iphone battery draining so fast 13 easy fixes.
Identify Mystery Numbers: How to Find No Caller ID on iPhone
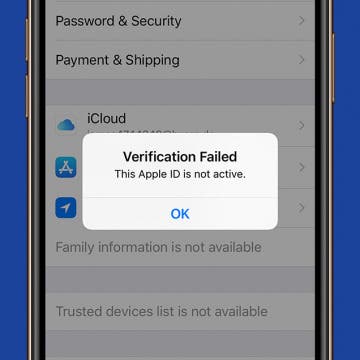
Apple ID Not Active? Here’s the Fix!
How to Cast Apple TV to Chromecast for Easy Viewing
Fix Photos Not Uploading to iCloud Once & for All (iOS 17)
There Was an Error Connecting to the Apple ID Server: Fixed
CarPlay Not Working? 4 Ways to Fix Apple CarPlay Today
Check out our sponsors.

- Each email reveals new things you can do with your phone (and other devices) with easy-to-follow screenshots.
- Enter your email to get your first tip immediately!
Award-winning news, views, and insight from the ESET security community
Mobile Security
Can your iPhone be hacked? What to know about iOS security
Here are some of the most common ways that an iPhone can be compromised with malware, how to tell it’s happened to you, and how to remove a hacker from your device

André Lameiras
19 Sep 2022 • , 7 min. read

Let’s be clear: if your iPhone or iPad is connected to the internet, there’s a risk it might get hacked. Sure, statistics seem to support the idea that your iOS device is pretty safe (and Apple keeps adding new safety features ), but your security largely hinges on how you actually use the device.
In this article, we’ll look at some of the most common ways for malware to compromise iPhones, some warning signs your own phone may have been hacked, and how to ‘fight back’.
How can an iPhone be hacked?
Sideloaded apps.
One of the biggest complaints about iOS is how slow the operating system is in adopting features that have long been present on Android devices. So to overcome this, some users resort to an option that goes against Apple’s Terms and Conditions: they jailbreak their phone.
This bypasses the built-in limitations to content from Apple’s App Store, allowing users to sideload apps and widgets from third-party stores. Sideloading – the act of getting an app from an unofficial store – can also be done by downloading it directly through a website on Safari or any other browser.
While allowing, or not, access to content from third-party stores can be debatable , as of now, only the applications on the App Store have been officially reviewed for safety. Meanwhile, the risks are clear: when installing a non-verified app, you are giving it unrestricted access to your device.
Fake apps in the App Store
Apple’s official store on your iOS device is generally known for providing safe content. Any application made available on the App Store has gone through a process that checked for bugs, privacy policy concerns, identification of third-party ad providers, and licensing requirements.
But sometimes a bad app(le) slips through the safety net. And a simple calendar event spam, a malicious link shared via messaging apps, or an aggressive advertisement displayed while browsing a website can open the App Store and suggest that you to install one of these inaccurately reviewed apps.
And because they are on the official store, there’s no reason to doubt their authenticity, right? Wrong. Such a dodgy app will try to cash in by, for example, selling you something you don’t need (and that doesn’t work) using Apple’s own in-app purchase system.
Calendar invites
Your iPhone’s Calendar app might seem like the safest place on your device, but it is actually one of the most common ways to distribute malware on iOS. Just like anyone you’ve just met can send you a Calendar invitation for a coffee later that week, hackers can do the same!
These unwanted invites can come from leaked email addresses or from you after unintentionally subscribed to calendar events on dodgy websites. Remember that scams are designed for people to fall for them. So in case you do, unsubscribe from the calendar and never tap on individual events you don’t know and trust as they will lead you to more spam.
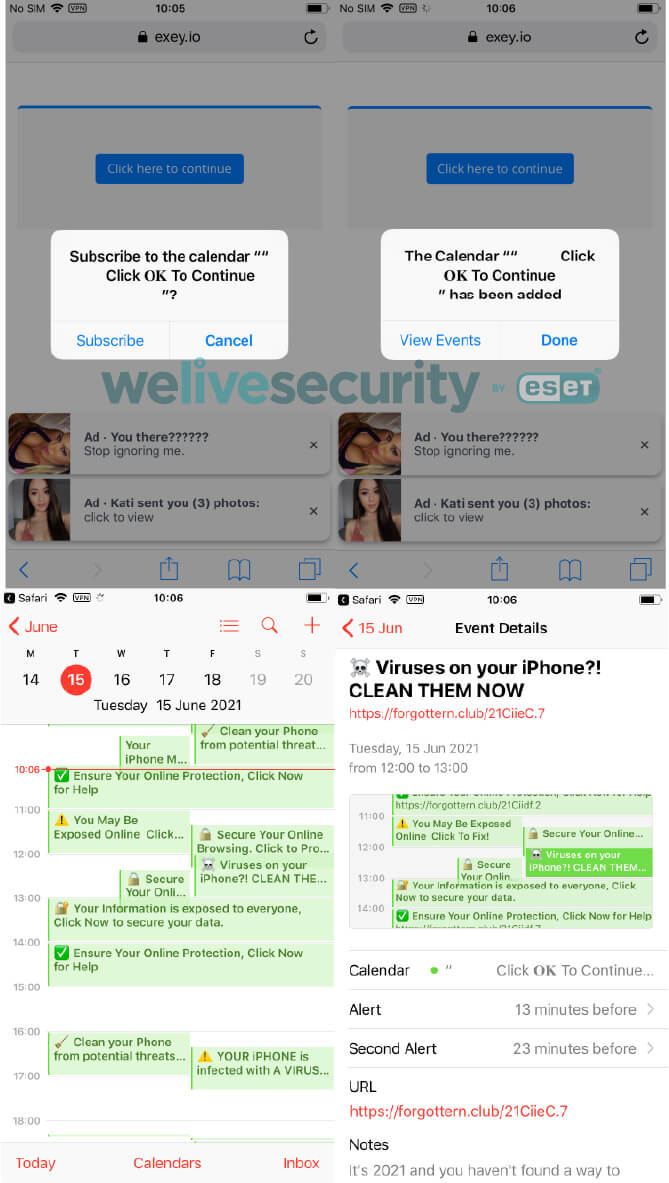
Figure 1. Scam website requests a user to subscribe to calendar events on iOS
Configuration profiles
Back in 2010, Apple made it possible to add configuration profiles to its iOS devices. This way, companies could manage on their iPhones a series of specific settings and functions as well as install apps used internally that do not need to be publicly available on the App Store.
While this is a useful tool for the legitimate use of companies and schools, hackers learned to take advantage of this feature . As usual, through phishing attacks and social engineering traps, hackers can lead their victims into tapping a link that will install a malicious configuration profile, granting them access to your Wi-Fi, VPN settings, app management, or internet traffic.
More than just the privacy and safety risks posed by this kind of threat, most users are not aware of profile management options, giving hackers the time needed to explore and exploit user’s password, steal banking information, or even install spyware .
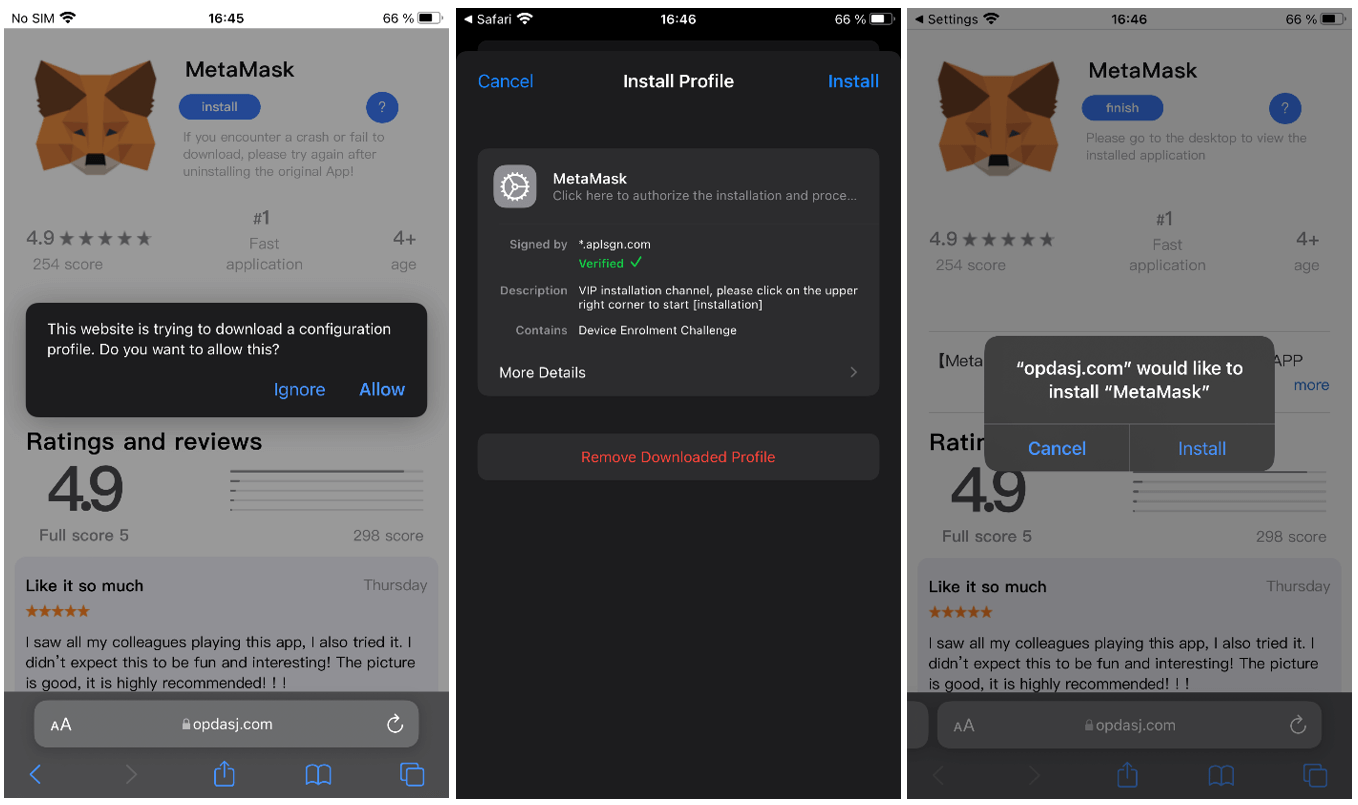
Figure 2. Malicious cryptocurrency wallet app installed via a configuration profile
The risks are real
If getting spam on your calendar sounds like a minor risk, having someone tracking you might sound much worse. But the most vicious thing about this type of hacking is that they are all interconnected. What was initially a small spam event invitation can easily escalate to installing a sideloaded app or a malicious configuration profile.
Bear in mind that your phone can also fall in the wrong hands without you noticing. This can be particularly sensitive in the context of abusive relationships. Stalkerware – a tool used to access your devices remotely – can be installed on your phone without your consent. Attackers can then target your personal information on iCloud, track your location, or access your photos and notes.
How can I tell if my iPhone has been hacked?
If you suspect or fear your iPhone has been hacked, there’s a few things you can check to start with:
- Battery levels: Batteries naturally wear down over time. However, if your device is just a few months old, battery draining too fast might be a sign of unexpected background activity. Check what apps are using battery and your battery health to discard this option.
- Data: If you’re not a heavy user of your mobile data plan, but you still reach its limits very fast, there’s a chance your iPhone has been hacked. Hidden software on your device might be using your data to pass on information. Keep in mind, however, the most likely is that you’re giving permission for some app to work on the background.
- Strange “things”: Is there an app on your iPhone that you don’t remember downloading? Or maybe an app that seems duplicated? These might be clears signs your device has been hacked. Attackers may attempt to install this content on your phone through a sideloaded app and even if are tech-savvy, you can be vulnerable to these ploys.

Figure 3. One of the two apps is an imposter (source: ESET research )
How do I remove a hacker from my iPhone?
- Check whether your device is jailbroken. Whether you’ve been hacked or you’re being stalked, you might not be aware that your phone has been jailbroken by someone else. As Apple now allows for apps to be removed from the Home Screen, use the search function to find jailbreaking apps like Cydia or Sileo. If you find them, fully restore your device to factory settings.
- Delete unnecessary apps and configuration profiles. If you have apps you’re not using, like wallpaper or weather apps , delete them. Even if they are safe, they might be tracking and selling your data to third parties. Also remove any configuration profiles that have not been installed by your organization or school.
- Check your apps’ settings. Take the time to use the Settings app to go through all your installed apps and check the permissions you give them. Know which apps you've given permission to use your location , and remove that consent from apps that don’t need it.
- Erase your iPhone or iPad content and settings. Make sure you have a backup of your photos and documents before fully restoring your device. Once you turn it back on, it will be clean from any malware and you can simply log in with your Apple ID to make it your own once again.
Figure 4. Giving an iPhone a fresh start
Can I prevent being hacked?
Everybody can fall victim to a cyberattack, but you can minimize your risks by following a few simple steps.
- Do not jailbreak your iPhone. Resist the temptation. There might be a lot of cool features out there, but the dangers are not worth it . Plus, jailbreaking voids your device’s warranty!
- Do not install third-party apps. There are thousands of apps on the official store. If you choose an iPhone, try to stick to what is safe for you and your device.
- Be on the lookout for phishing scams. Don’t trick yourself into thinking that you won’t fall for scams; we all do. So beware of scam emails that request personal information and might steal account credentials .
- Do not open links from people you don’t know and recognize. This is simple advice but it will help you avoid a lot of headache.
- Use multi-factor authentication. If hackers take over your phone, prevent them from attacking your other accounts successfully. Add extra steps to protect your credentials .
- Use a VPN. It will bolster your privacy and data protection , particularly if you are using a public Wi-Fi network .
- Always keep your phone up to date. Make sure you are using the latest iOS update. Apple regularly adds new versions with new functionalities and, more importantly, safety patches to secure your devices.
In the end, no matter how likely you are to get hacked, it’s important to understand the risks and implement a few simple precautions. Avoiding to jailbreak your device, refraining from tapping on unfamiliar links, and using multi-factor authentication wherever it’s available will go a long way towards protecting your device and your data.
Let us keep you up to date
Sign up for our newsletters
Related Articles
Attack of the copycats: How fake messaging apps and app mods could bite you

These aren’t the Androids you should be looking for

Silent but deadly: The rise of zero-click attacks

Share Article

How to Tell if Your iPhone is Hacked: A Comprehensive Guide
Are you worried that your iPhone might be hacked? It’s a valid concern in today’s digital age where cyber threats are increasing. Fortunately, there are several signs to look out for that can indicate whether your iPhone has been compromised. In this article, we’ll guide you through the steps to determine if your iPhone has been hacked and provide tips on how to keep your device secure.
How to Tell if Your iPhone is Hacked
Before we dive into the steps, it’s important to understand that an iPhone hack can manifest in various ways. You might notice unusual behavior from your device, such as a sudden decrease in battery life, unfamiliar apps appearing on your home screen, or your personal data being accessed without your permission. The following steps will help you identify if your iPhone has been hacked.
Step 1: Check for Unusual Activity
Look for any strange activity on your iPhone, such as apps crashing frequently, unfamiliar texts or calls in your logs, or unexpected changes in your settings.
When an iPhone is hacked, the hacker may try to cover their tracks, but they can’t always hide their actions completely. Keep an eye out for anything that seems out of the ordinary, as it could be a sign that someone has unauthorized access to your device.
Step 2: Examine Battery Usage
Check your iPhone’s battery usage to see if there are any apps running in the background that you’re not aware of.
A sudden drop in battery life could be a sign of malicious software running on your iPhone. Go to ‘Settings’ > ‘Battery’ and look for any apps that are using a disproportionate amount of power, especially if you don’t recall using them.
Step 3: Look for Unknown Apps
Check your home screen and app folders for any apps that you don’t remember downloading.
Hackers often install their own apps to gain access to your data. If you find apps that you don’t recognize, it’s a red flag. Do not open these apps, as they could be designed to harvest your information or cause further harm to your device.
Step 4: Monitor Data Usage
Monitor your data usage to see if there’s an unexplained increase.
Unexpected spikes in data usage could indicate that your iPhone is transmitting data to an external server without your knowledge. Check ‘Settings’ > ‘Cellular’ to review your data usage and look for any anomalies.
Step 5: Run a Security Scan
Use a trusted security app to run a scan on your iPhone.
While iPhones are generally secure, it’s still a good idea to use a reputable security app to check for any threats. If the scan detects any issues, follow the app’s instructions to address them.
After completing these steps, you should have a clearer understanding of whether your iPhone is hacked. If you’ve found evidence of a hack, it’s crucial to take immediate action to secure your device and protect your personal information.
Tips for Keeping Your iPhone Secure
- Regularly update your iPhone to the latest version of iOS, as updates often include security enhancements.
- Avoid downloading apps from outside the App Store, as they may not be vetted for security.
- Use strong, unique passwords for your Apple ID and other accounts.
- Enable two-factor authentication for added security.
- Be cautious of phishing attempts and avoid clicking on suspicious links or providing personal information to unknown sources.
Frequently Asked Questions
What should i do if i think my iphone is hacked.
If you suspect your iPhone has been hacked, change your Apple ID password immediately, and consider resetting your device to its factory settings after backing up important data.
Can iPhones get viruses?
While it’s less common for iPhones to get viruses compared to other devices, it’s still possible, especially if the device is jailbroken or apps are downloaded from untrusted sources.
Is it safe to use public Wi-Fi on my iPhone?
Using public Wi-Fi can pose security risks, as it’s easier for hackers to intercept your data. Always use a VPN when connecting to public Wi-Fi networks.
How can I tell if an app is safe to download?
Only download apps from the Apple App Store, as Apple reviews all apps for security and compliance before making them available to users.
Can two-factor authentication prevent hacking?
Two-factor authentication adds an extra layer of security by requiring a second form of verification, making it much harder for hackers to gain access to your accounts.
- Check for unusual activity.
- Examine battery usage.
- Look for unknown apps.
- Monitor data usage.
- Run a security scan.
The thought of having your iPhone hacked can be unsettling, but by being vigilant and taking the necessary precautions, you can protect your device and your personal information. Remember to keep an eye out for any unusual behavior, regularly update your device, and be cautious of where you download apps from. If you do suspect that your iPhone has been compromised, act swiftly to secure your device and consider reaching out to Apple Support or a professional for assistance. Stay safe and happy surfing!

Matthew Burleigh has been writing tech tutorials since 2008. His writing has appeared on dozens of different websites and been read over 50 million times.
After receiving his Bachelor’s and Master’s degrees in Computer Science he spent several years working in IT management for small businesses. However, he now works full time writing content online and creating websites.
His main writing topics include iPhones, Microsoft Office, Google Apps, Android, and Photoshop, but he has also written about many other tech topics as well.
Read his full bio here.
Share this:
Join our free newsletter.
Featured guides and deals
You may opt out at any time. Read our Privacy Policy
Related posts:
- Why Is My iPhone Battery Yellow (2024 Guide)
- 15 iPhone Settings You Might Want to Change
- Is My iPhone 13 Battery in Good Shape?
- How to Silence Apple Watch
- How to Change Battery Saver Threshold in Windows 10
- How to Make All Columns the Same Width in Excel 2013
- How to Check Battery Health on iPhone 14
- iOS 17 Guide: How to Turn On/Off Battery Percentage on iPhone
- How to Delete Apps on iPhone 8
- How to Display Battery Percentage on iPhone 5
- How to Hard Reset iPhone 11 (2024 Guide)
- How to Rotate Screen on iPhone 7
- How to Keep iPhone Screen On (2023 Guide)
- How Long Is the Battery Life for the iPhone 5? Tips to Extend It
- How to Sign Out of iPhone 13 in iOS 15
- How Can You Check the Battery Level on an iPhone? A Step-by-Step Guide
- How to Change the Download Over Cellular iPhone Setting
- 10 Tips to Improve Battery Life on the iPhone 7
- Android Vs. IOS Battery Life: Which Lasts Longer?
- How to Change Screen Timeout on iPhone 13
- PRO Courses Guides New Tech Help Pro Expert Videos About wikiHow Pro Upgrade Sign In
- EDIT Edit this Article
- EXPLORE Tech Help Pro About Us Random Article Quizzes Request a New Article Community Dashboard This Or That Game Popular Categories Arts and Entertainment Artwork Books Movies Computers and Electronics Computers Phone Skills Technology Hacks Health Men's Health Mental Health Women's Health Relationships Dating Love Relationship Issues Hobbies and Crafts Crafts Drawing Games Education & Communication Communication Skills Personal Development Studying Personal Care and Style Fashion Hair Care Personal Hygiene Youth Personal Care School Stuff Dating All Categories Arts and Entertainment Finance and Business Home and Garden Relationship Quizzes Cars & Other Vehicles Food and Entertaining Personal Care and Style Sports and Fitness Computers and Electronics Health Pets and Animals Travel Education & Communication Hobbies and Crafts Philosophy and Religion Work World Family Life Holidays and Traditions Relationships Youth
- Browse Articles
- Learn Something New
- Quizzes Hot
- This Or That Game New
- Train Your Brain
- Explore More
- Support wikiHow
- About wikiHow
- Log in / Sign up
- Computers and Electronics
- Cell Phones
- Cell Phone Maintenance
How to Remove a Hacker from Your iPhone
Last Updated: February 9, 2024 Tested
This article was written by Aydin Yildiz and by wikiHow staff writer, Nicole Levine, MFA . Aydin Yildiz is an Electronics Repair Specialist and the Founder of Aasha Inc. With more than five years of experience, he specializes in phone, tablet, and computer repairs. Aydin holds an MBA from Southern States University. The wikiHow Tech Team also followed the article's instructions and verified that they work. This article has been viewed 281,533 times.
We use our iPhones for everything—managing our appointments, communicating with friends and family, online banking, and even tracking our health data. The fact that our iPhones contain so much of our personal information makes them attractive targets for unethical hackers. This wikiHow article will teach you how to figure out if your iPhone's been hacked, and some easy steps you can take right now to get rid of the hacker for good.
What are some signs my iPhone is hacked?

- Apple is fairly strict about the apps it allows on the App Store. If you've jailbroken your iPhone or have downloaded apps from anywhere other than the App Store, you're more likely to wind up with shady apps on your phone.
- If you share your iPhone with someone else (or are using Family Sharing features), apps you don't recognize may have been installed by someone you actually trust. Before you panic, check with other members of your family to see if anyone installed the unfamiliar apps.

- If you're browsing the web and see a pop-up that says "Your iPhone has been compromised!" or "We have detected that your browser is infected with a trojan virus," this doesn't mean you were really hacked. In most cases, these pop-ups appear when you click on a website that's malicious (or has been hacked).
- Never click a link or provide any sort of payment in response to one of these pop-up messages. You should never have to pay to remove any sort of virus from an iPhone.

- Open your Settings , tap General , and then tap Profiles & Device Management . [1] X Research source If you see any profiles you don't recognize, a hacker may have tricked you into installing it.
- If you don't see this section in your Settings at all, don't panic. It just means you don't have any configuration profiles installed.

- If you sign into another Apple device (like your family Mac, your partner's iPad, or your child's iPhone) with the same Apple ID you use on this iPhone, you may see the calls and texts they've sent while signed in with your ID. Ask your family members whether they've made the calls or sent the messages before assuming your iPhone is hacked.
- In this case, it's a good idea to contact your provider and ask for help to recover your account.

- Open your Settings app and tap Cellular or Mobile (depending on your region). Scroll down to the "CELLULAR DATA" or "MOBILE DATA" section to see which apps are using a lot of data. If you see something you don't recognize, be wary.

- Sometimes your iPhone can get excessively warm when you're playing games or using other CPU-intensive apps—it doesn't always mean you were hacked.

How do I get rid of a hacker?

- To disconnect quickly, swipe down from the top-right corner of the Home screen (if your iPhone doesn't have a Home button) or swipe up from the bottom (if it does have a Home button), and then tap the airplane icon to go into Airplane Mode. If your phone stays connected to Wi-Fi in airplane mode, tap the Wi-Fi icon (the curved lines) to disconnect.

- Safari: Open Settings , tap Safari , and then scroll down and tap Clear History and Web Data . Tap Clear History and Data to confirm.
- Chrome: Open Chrome, tap the three dots at the bottom-right, select History , and then tap Clear Browsing Data . Select All Time as the time range and tap Clear Browsing Data at the bottom.

- When you restore from a backup, you're also resetting your iPhone. This erases everything on your iPhone! But as long as you'ved back up or sync your data to iCloud or your computer, you can restore from your backup after resetting.

How can I keep hackers out of my iPhone?

- To turn on automatic iOS updates, go to Settings > General > Software Update > Automatic Updates and toggle both switches to the On (green) position.
- To turn on automatic app updates, go to Settings > App Store > and toggle App Updates to the On (green) position.

- To turn on two-factor authentication, open Settings , tap your name at the top, tap Password & Security , and then tap Turn on Two-Factor Authentication (if it's not already on).
Brandon Phipps
Enable two-factor authentication on all your digital accounts. That applies to all your personal accounts, business accounts, finances, client information, and productivity apps. Two-factor authentication protects your sensitive data from unauthorized parties and reduces the risk of security breaches.

- If an app you've installed asks to access your microphone, camera, Bluetooth, photos, or anything else you don't feel comfortable sharing, deny that app permission when prompted. In some cases, the permission is needed for the app to function, but you can allow it only when the app is being used to minimize risks.
- If an app or website ever prompts you to install a profile, don't do it—profiles can give hackers access to your phone.

Expert Q&A
You Might Also Like

- ↑ https://support.apple.com/guide/iphone/install-or-remove-configuration-profiles-iph6c493b19/ios
- ↑ https://support.apple.com/en-us/HT205347
- ↑ https://rocketit.com/signs-your-iphone-was-hacked-how-to-remove-virus/
- ↑ https://support.apple.com/en-us/HT201222
About This Article

1. Disconnect from the internet. 2. Remove unfamiliar apps and configuration profiles. 3. Clear your browsing history. 4. Restore from a backup. 5. Update your iPhone. 6. Change your password. 7. Reset your iPhone if necessary. Did this summary help you? Yes No
- Send fan mail to authors
Is this article up to date?

Featured Articles

Trending Articles

Watch Articles

- Terms of Use
- Privacy Policy
- Do Not Sell or Share My Info
- Not Selling Info
wikiHow Tech Help Pro:
Level up your tech skills and stay ahead of the curve
Your iPhone Has Been Compromised, (And How It Really Hasn't)

Here we are again, in an iPhone-centric bit of not-really-real mishap, this time centered on the word "Compromised." That's a scary word and term, almost as scary as something like "your internet history is now public." But take heart, there is no need for alarm if you've only just seen the pop-up. Today we're going to have a chat about how to avoid such things and how to destroy the pop-ups you've got already.
No, Sharon, your iPhone is not compromised
You're a SlashGear reader, right? You've almost certainly got more than a couple computer-illiterate people in your life, people that believe whatever's written and do whatever they're told. If it looks like it's important, it must be true! That's the way of the past – the way of person-to-person trust, and it's not a way that's ever really gone according to plan when it came to the internet.
The latest example of this compromise scam includes a sort of pop-up. An advertisement button will appear on your iPhone and will say one of the following super scary and/or exciting messages.
Malicious iOS pop-up contents could potentially include:
• Amazon Prize Winner notification
• WARNING! This Apple iPhone is corrupted with virus and battery has been damaged!
• Continue with instructions to fix phone. Do not close window.
• Forewarning! This cellular phone carries a trojan. CALL (number)
• You've been selected for a chance to get the $1000 Amazon Gift Card
• Your iPhone has been compromised / Immediate action is required!
• Police Locked iPhone
• Your credit card is at risk!
• FBI locked down iPhone
• Any mention of spyware or offer to provide help with a phone number
If you see any of the messages above, or even any messages at all similar, you're the target of a scammer. Their message most likely got inserted in a webpage, where it lives to deceive. If you've only just seen the message in a pop-up, you're still safe. Nothing's been hijacked but the webpage from whens the message came.
How to fix the pop-up
The pop-ups outlined above generally come from your iPhone's internet browser, from webpages you've visited in the past. To get rid of this nonsense, you'll want to attempt to follow the steps outlined here:
Safari Pop-up scam fix:
• Swipe up to access your quick settings, or just go to Settings
• Activate Airplane Mode
• Go to Settings, scroll down to Safari, tap to open, tap Clear History and Website Data (as shown below)
• Double-click your home button or swipe up from the middle of your home screen, find your Safari pane, and swipe up (and away to close)
• Restart your phone
• Turn off Airplane Mode
Google Chrome Pop-up scam fix:
• Open the Chrome browser app
• Tap the three dots in the lower right-hand corner of the screen
• Tap Settings, then Privacy
• Tap in to the Clear Browsing Data submenu
• Check off Browsing History, Cookies, Site Data, and Cached Images and Files by tapping on them
• Tap Clear Browsing Data
• There'll probably be a confirmation alert at this point, through which you will actually clear your browsing data and that nasty pop-up
This SHOULD relieve you of your most-hated piece of the internet, that pop-up that makes so very many promises. Remember, no matter how many times you see it, it doesn't suddenly become true. Even if it gives you a phone number to call, you call, and there's a real person on the other end of the line – that person is a scammer, too.
One more warning for good measure
This is a time of transition. Especially if you're the sort of person that likes to get all of your iPhone's most important updates at all times, you MAY be the target of scammers preying on your wishes to remain up-to-date at all times.
We've not heard of or seen this particular scam any time lately, which makes us think that scammers may have become more crafty in picking their targets than they've been in the past. Just remember: only download software from the sources you know and trust, and if you want to avoid scams altogether, just stick to the basics!
Remove “Your iPhone has been hacked” pop-up ad
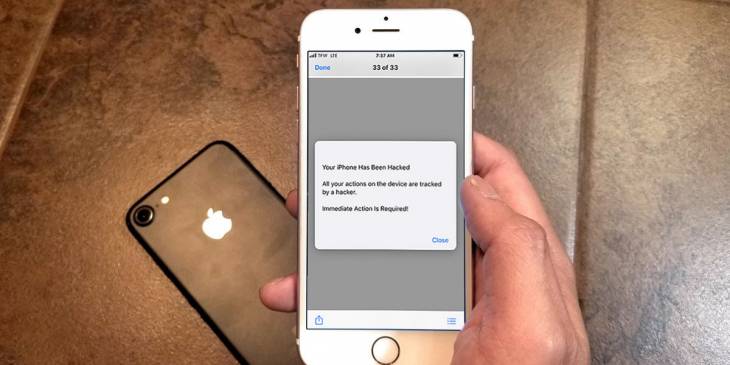
This article explains the logic of ‘Your iPhone has been hacked’ scam campaign and provides steps to remove this pop-up ad from an affected Apple device.
What is ‘Your iPhone has been hacked’ scam?
Although there are different shades of hacking that run the gamut from ethical and jailbreak-type to black hat and government-funded attacks, this term instills fear in most users regardless of the implications. With this in mind, some cybercriminal gangs boil their fraudulent activities down to a pseudo-hacking theme in an attempt to increase the success rate of getting people on the hook. This is the case with a social engineering wave that involves deceptive popup alerts to dupe Apple fans into making bad decisions. This message is generated by a dubious web page and says,
“Your iPhone has been hacked. All your actions on the device are tracked by a hacker. Immediate action is required!”
The source of this misleading notification can be twofold. It’s usually a series ofad scripts running on a malicious site created by malicious actors. However, in some scenarios the fraud is fueled by a takeover of a legitimate website through vulnerable plugins or weak, and hence easily crackable passwords used by webmasters. At the time of writing, there are a handful of dodgy and previously breached pages serving these popup ads to all visitors.
Special Offer “Your iPhone has been hacked” popup virus may re-infect your Mac multiple times unless you delete all of its fragments, including hidden ones. Therefore, it is recommended to download Combo Cleaner and scan your system for these stubborn files. This way, you may reduce the cleanup time from hours to minutes. Download Now Learn how ComboCleaner works . If the utility spots malicious code, you will need to buy a license to get rid of it.
The purpose of “Your iPhone has been hacked” fake alerts
The operators of this scam seek to take advantage of the primary infection to deposit second-stage payloads onto unsuspecting people’s devices. Although the user interaction facet of different variants of this popup is isolated to the “Close” or “OK” button, tapping or clicking on it doesn’t do what is expected. Instead, it opens an additional tab in Safari, Google Chrome, or Mozilla Firefox, that displays a follow-up warning about dozens of viruses supposedly found in the system. If this phony page is closed, the relief won’t last: the browser hijacker that’s already inside the system will be circling back to its manipulative brainwashing method over and over. The potentially unwanted applications (PUAs) promoted this way include adware, Trojans, info-stealing threats, fake system maintenance tools, and screen lockers.
Who is at risk?
Although the wording of “Your iPhone has been hacked” popup suggests that the range of targeted devices is entirely in the iOS area, computers running macOS are potentially susceptible to the same exploitation, too. Therefore, in addition to the iPhone or iPad, the issue can make itself felt on MacBook Air and MacBook Pro laptops, as well as iMac and Mac Pro machines. Obviously, it doesn’t make a whole lot of sense, and yet the increased interoperability between different Apple products, plus a good deal of shared features across mobile and desktop ecosystems, makes this scam cross-platform. Another consideration is that the alert originates from a sketchy website that can just as well be visited from a computer. No matter what device is hit, the underlying principle of the attack is all about a piece of malware that sneaks in and modifies the settings of the victim’s default browser. This tampering entails incessant redirects that lead to a site hosting the spoofed warning.
Dealing with “Your iPhone has been hacked” pop-up ad virus: dos and don’ts
First things first, keep in mind that your device hasn’t been hacked for real. This is a stubborn fake popup triggered by a harmful site or a PUA that slithered its way into your system. Secondly, installing any apps pushed by this alert and the subsequent related web pages is not a good idea. This campaign is all about pressuring users into authorizing the infiltration of extra threats. So, ignoring the information on this ad is half the battle. It won’t stop deluging the device on its own, though, and therefore malware cleaning is on a victim’s to-do list. The following sections include point-by-point instructions to sort out the problem on an iOS and a macOS device.
“Your iPhone has been hacked” message manual removal for iOS (iPhone, iPad)
As per the anatomy of this hijack, settings of the web browser that may have gotten hit by the virus should be restored to their default values. The steps for performing this procedure are as follows:
- Safari troubleshooting on iPhone / iPad
- Go to Settings and select Safari on the menu.
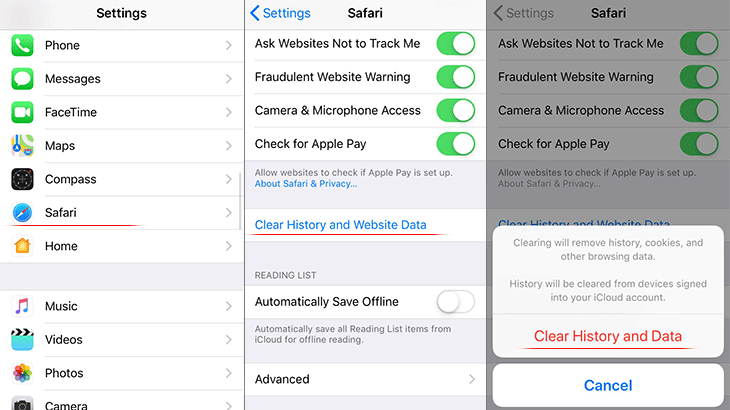
- Confirm by tapping Clear History and Data . Check if the problem with Safari has been fixed. In the event the iPhone / iPad virus popups are still there, proceed to the next step.
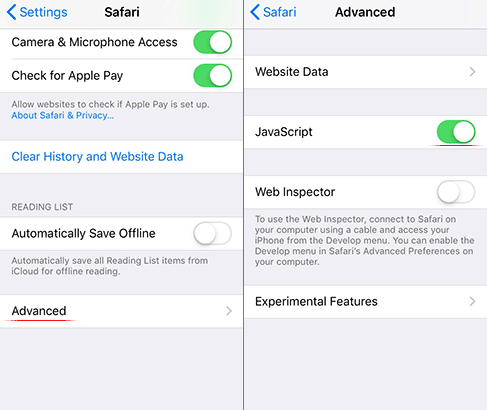
- As the menu expands, make sure the following options are checked: Browsing History ; Cookies, Site Data ; and Cached Images and Files . Now, tap Clear Browsing Data and confirm before exiting. The popup and redirect activity should now stop in Chrome.
“Your iPhone has been hacked” pop-up ad manual removal for Mac
The steps listed below will walk you through the removal of this malicious application. Be sure to follow the instructions in the specified order.
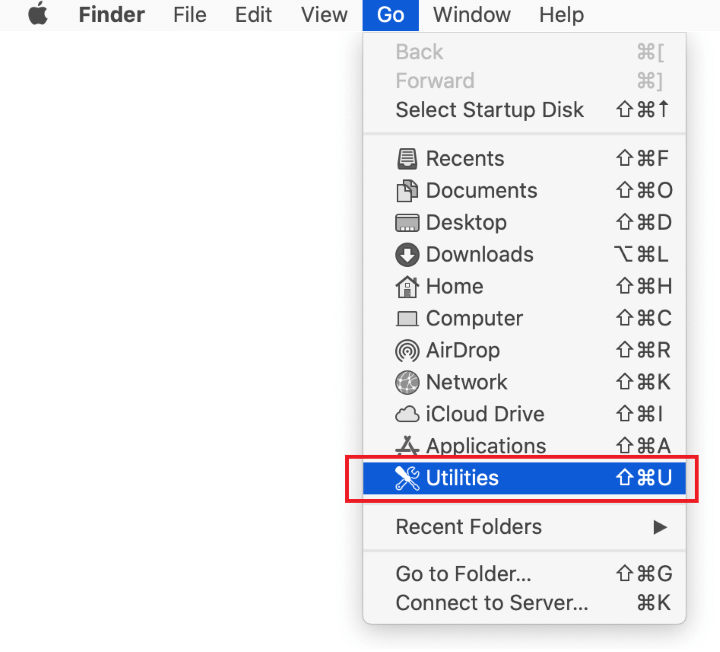
As an illustration, here are several examples of LaunchAgents related to mainstream Mac infections: com.pcv.hlpramc.plist, com.updater.mcy.plist, com.avickUpd.plist, and com.msp.agent.plist . If you spot files that don’t belong on the list, go ahead and drag them to the Trash.
Get rid of “Your iPhone has been hacked” virus in web browser on Mac
To begin with, the web browser settings taken over by the “Your iPhone has been hacked” virus should be restored to their default values. Although this will clear most of your customizations, web surfing history, and all temporary data stored by websites, the malicious interference should be terminated likewise. The overview of the steps for completing this procedure is as follows:
- Restart Safari
- When on the Settings pane, select Advanced
- Confirm the intended changes and restart Firefox.
Get rid of “Your iPhone has been hacked” virus using Combo Cleaner removal tool
The Mac maintenance and security app called Combo Cleaner is a one-stop tool to detect and remove “Your iPhone has been hacked” virus. This technique has substantial benefits over manual cleanup, because the utility gets hourly virus definition updates and can accurately spot even the newest Mac infections.
Furthermore, the automatic solution will find the core files of the malware deep down the system structure, which might otherwise be a challenge to locate. Here’s a walkthrough to sort out the “Your iPhone has been hacked” issue using Combo Cleaner:
Download Combo Cleaner
By downloading any applications recommended on this website you agree to our Terms and Conditions and Privacy Policy . The free scanner checks whether your Mac is infected. To get rid of malware, you need to purchase the Premium version of Combo Cleaner.
- Open the app from your Launchpad and let it run an update of the malware signature database to make sure it can identify the latest threats.
- Once you have made doubly sure that the malicious app is uninstalled, the browser-level troubleshooting might still be on your to-do list. If your preferred browser is affected, resort to the previous section of this tutorial to revert to hassle-free web surfing.
Was this article helpful? Please, rate this.
Apple is stepping up app verification through new App Attest API
Macros vs macos: advanced exploit chain targeting macs.
Poppy Mot - 3 years ago
Authentication required.
You must log in to post a comment.
Can My iPhone Be Hacked Through Safari?
By Sophia Taylor
Published: February 2, 2024
More than 800 million people use Safari on their iPhones to browse the web—but is this app safe to use?
While Safari includes various security features to protect your phone from hacking, it’s still possible for hackers to gain access to your device through this app.
In fact, it has happened many times before.
A group of researchers recently discovered a method to access iPhones through Safari, enabling them to collect sensitive data from these devices by creating fake websites.
In this guide, we will discuss iPhone hacking through Safari and the steps you can take to safeguard yourself. We’ll also explain what you can do if you suspect your phone has been hacked.
Can iPhones Get Hacked Through Safari?
Cyberattacks against Safari happen all the time. In 2023 alone, there were 41 Safari exploits discovered , of which 11 were known to have been actively exploited by hackers. However, due to the complexity of these exploits and speed at which Apple fixes them, it is probably unlikely that it will happen to you.
For example, in November 2023, Apple was made aware of an attack where cybercriminals were using WebKit, the browser engine for Safari, to hack iPhones through the app in two ways:
❌ Manipulating WebKit to read the memory and sensitive information on an iOS device.
❌ Using WebKit to run code that can download malware—malicious software designed to spy on devices —onto an iPhone.
Although Apple hasn’t disclosed the details of the attack, they have since released a security patch to address the issue.
This was designed to fix the exploited vulnerabilities and ensure that cybercriminals could no longer use this particular approach to hack Apple devices.

🤔 What about Advanced Spyware?
How ios is structured to avoid safari hacking.
Apple is renowned for its stringent approach to security. For example, third-party apps are rigorously vetted before they can appear on the Apple App Store, which protects iPhone users from downloading malicious apps.
The manufacturer also uses something called sandboxing, which is how they restrict third-party apps—including Safari—from accessing your files and data or making changes to your device.
Lastly, Apple is among the best when it comes to releasing regular security updates for their devices. Their Security Bounty program also incentivizes security researchers to report any discovered vulnerabilities to Apple as quickly as possible.
Therefore, by installing the latest iOS updates as soon as they become available you can stay protected against the vast majority of iPhone vulnerabilities and exploits.
How to Prevent Your iPhone from Being Hacked Through Safari
Aside from ensuring you always have the latest version of iOS installed on your iPhone, there are some other things you can do to prevent being hacked through Safari.
✅ Only download apps from Apple’s App Store
Some people jailbreak their iPhones to download apps that aren’t approved by Apple and don’t appear in the App Store.
However, downloading these apps can quickly result in spyware being installed on your iPhone, meaning a hacker can:
- Steal your sensitive data, like your banking information.
- Access your photos and videos.
- Monitor your text messages.
- Listen to your voice calls.
✅ Be cautious of the websites you visit
Think carefully about following a link to a website you don’t recognize. This link could lead you to a fake or malicious website designed to steal your data and hack your phone.
Many people fall victim to phishing attacks by visiting websites that look legitimate and then entering their personal information on these sites. Hackers then use this information to access your online accounts.
✅ Block pop-ups
Some pop-ups are designed for phishing attacks.
For example, you may encounter a pop-up announcing that you’ve won a prize and urging you to visit a specific website.
You visit this website and enter your personal details to redeem your prize. However, this is a malicious site, and hackers are using it to steal sensitive information.
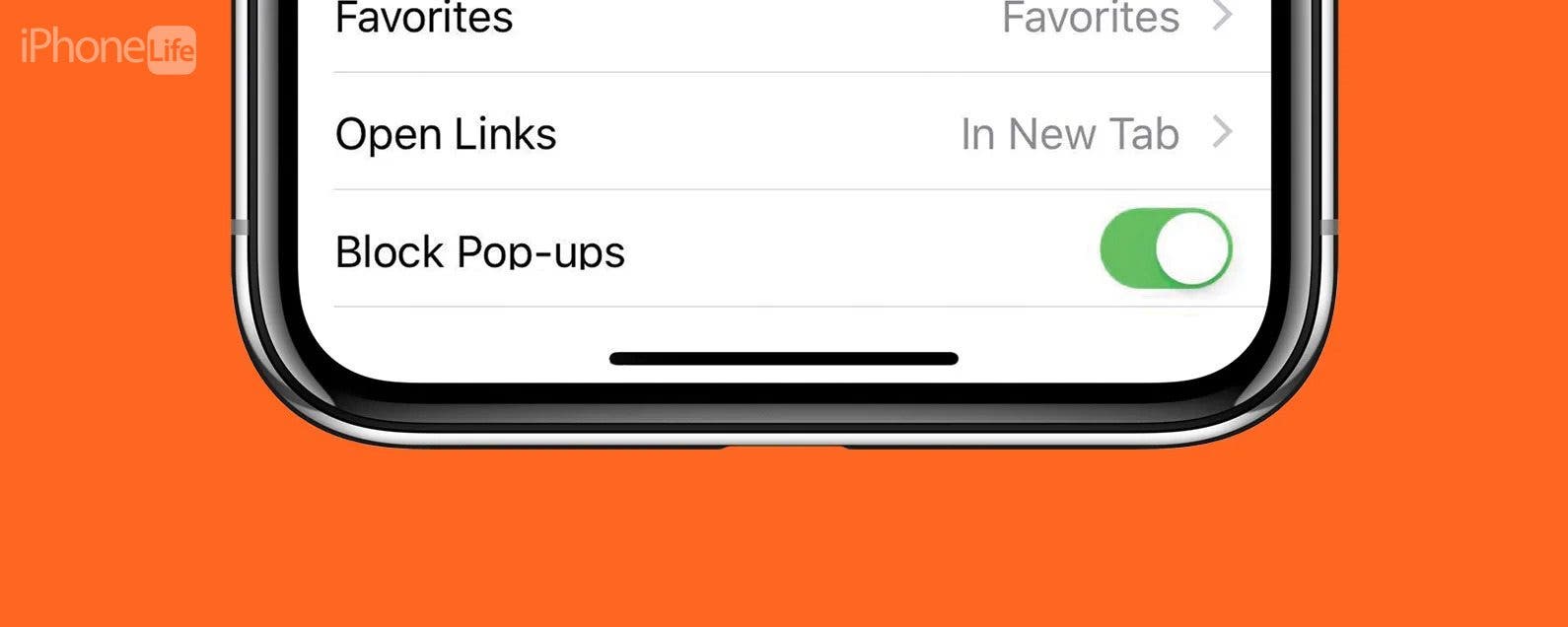
This is why it’s a good idea to block pop-ups on Safari. To do this:
- Open Settings and tap Safari.
- Turn on Block Pop-ups.
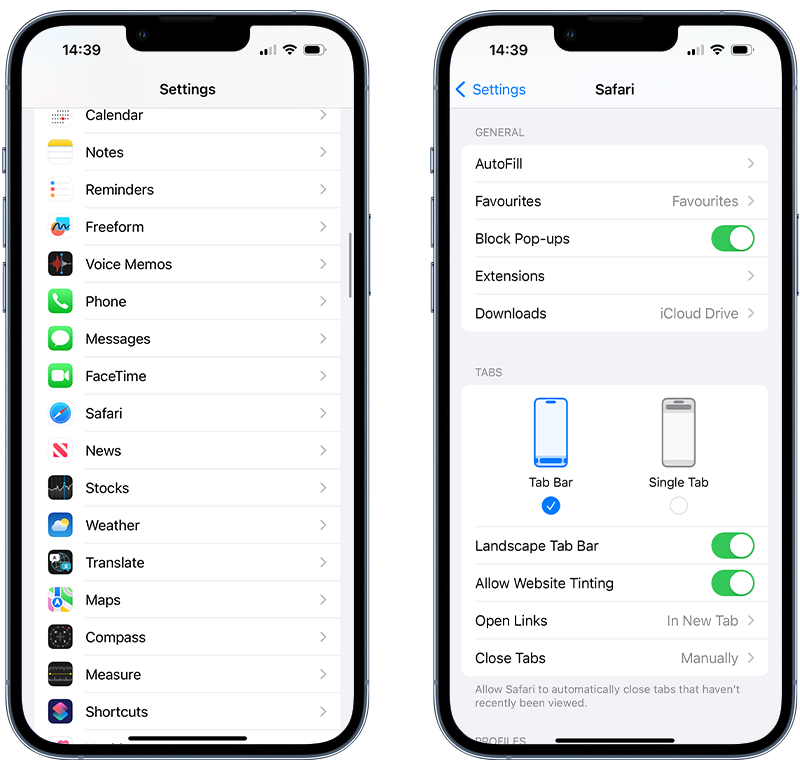
Fig 1. Blocking Safari pop-ups on iPhone.
✅ Change your Safari settings
There are multiple privacy settings in Safari that you can adjust on your iPhone to enhance your browsing safety. You can do this by visiting Settings > Safari and then toggling the sliders to turn on features that will:
- Prevent cross-site tracking: This limits Safari from collecting third-party cookies and data that can be used to track your browsing activity.
- Hide IP your address: This conceals your iPhone’s IP address from known trackers, another way to prevent your activity and personal information from being tracked.
- Warn you if a website is fraudulent: This will alert you if a website you visit is a suspected phishing website.
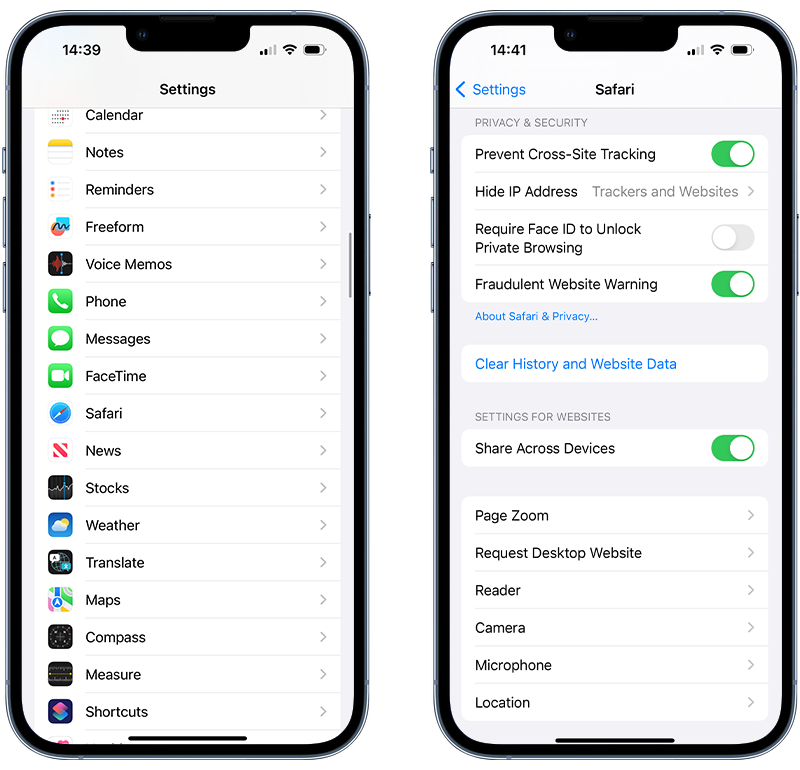
Fig 2. Safari privacy settings on iPhone.
✅ Control Safari access to device features
Websites can use your camera, microphone or location when you visit them using Safari. This can be useful if you need to upload a photo or provide a site with your exact location, but some malicious websites have been known to misuse this data.
You can set up Safari so that websites must either request permission before accessing these features or are blocked from using them altogether. This is a good way to limit potential data leakage when using Safari.
To check these settings:
- Scroll down and tap either Camera, Microphone or Location.
- Choose either Ask or Deny.
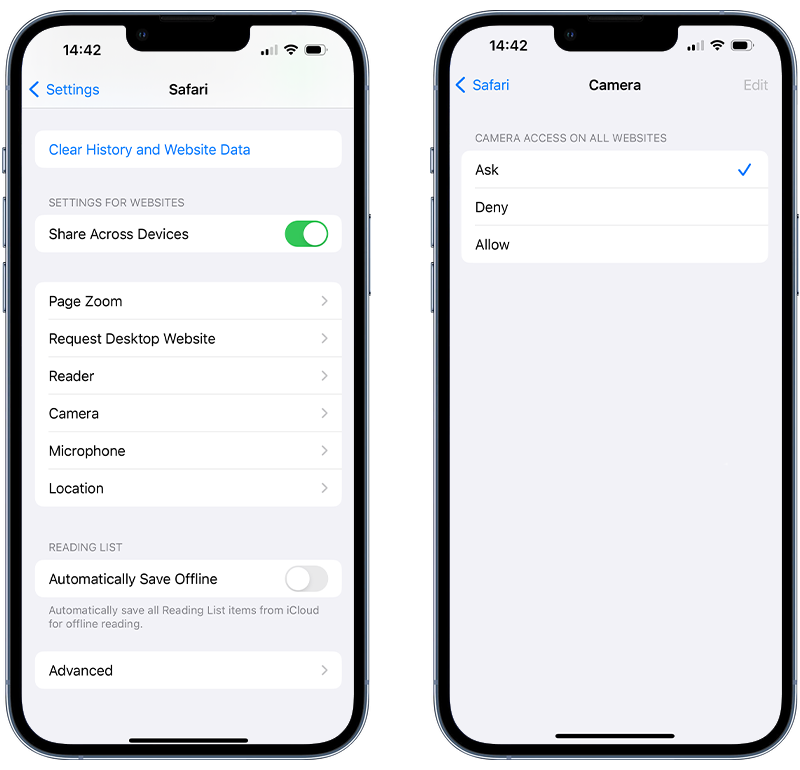
Fig 3. Checking access to device features in Safari.
✅ Use iCloud Private Relay
If you’re subscribed to iCloud+, you can use the iCloud Private Relay to prevent websites from collecting information about you.
When this feature is turned on, the information leaving your iPhone while you browse is encrypted, which means it’s nearly impossible for hackers to spy on it.
This also prevents websites from seeing your IP address and location and collecting your browsing activity on Safari.
To turn on iCloud Private Relay:
- Go to Settings.
- Tap your name.
- Navigate to iCloud.
- Tap Private Relay.
- Toggle the slider to green.
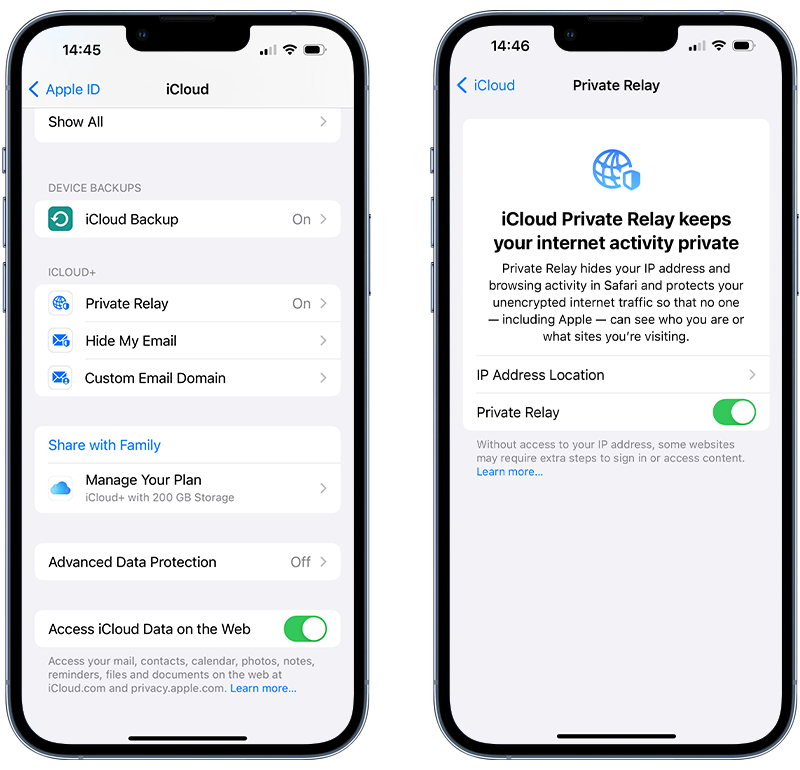
Fig 4: Enabling iCloud Private Relay.
✅ Use an additional security app
There are several apps which have been vetted by Apple that you can use to enhance security on your iPhone. They provide additional safety settings that you can enable to protect your phone.
One such app is Certo Mobile Security , which is free and can:
- Scan your phone for vulnerabilities.
- Run a security health check.
- Check your WiFi network for signs of compromise.
- Help you set up your iPhone for optimal security with detailed instructions of how to configure over 20 additional iOS settings.
A security app can provide you with extra peace of mind that your iPhone is protected against hacking and cyber attacks.
What Can I Do if My iPhone Has Been Hacked Through Safari?
Although the chances of being hacked through Safari are slim, there are some things you can do if you think it has happened to you:
➡️ Remove apps you don’t remember downloading
One way to remove potential malware is to uninstall any apps that you don’t recognize.
Visit your app library and look for any apps you don’t recognize. Here’s how to find and remove them:
- Open Settings and tap General > iPhone Storage.
- Review the list and check for any apps you do not recognize.
- Tap on any unrecognized apps and tap Delete App to remove it from your iPhone.
➡️ Scan your phone for spyware
Some Safari exploits may try to install spyware on your device, providing a hacker with complete remote access to your device.
If you suspect your iPhone has been hacked, you can use an anti-spyware tool like Certo AntiSpy to perform a deep scan of your phone. This can help to detect hidden spyware and remove threats from your device.
Here’s how to secure your iPhone with Certo AntiSpy:
- Download Certo AntiSpy to your computer.
- Plugin your iPhone and click Scan.
- Tap Remove next to any threats to safely remove them from your device.
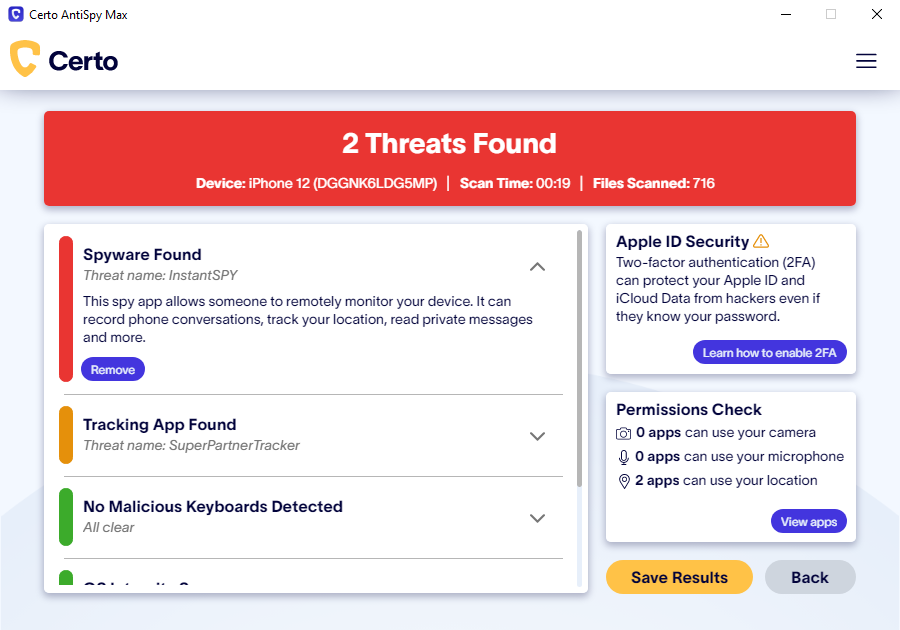
Fig 5: Detecting iPhone spyware with Certo AntiSpy.
➡️ Restore to factory settings
Another way to fix a hacked phone is to hard reset it back to its original state, known as factory settings. This wipes all the data and settings from your iPhone completely.
Before you do this, ensure that your data is backed up to iCloud so you can download it again once you reset your phone. Don’t worry, any malware on your phone won’t get backed up to iCloud with your data.
To reset to factory settings:
- Open Settings.
- Navigate to General.
- Select Transfer or Reset iPhone.
- Tap on Erase All Content and Settings.

Fig 6: Performing a factory restore on iPhone.
Wrapping Up
While the prospect of iPhone hacking through Safari may seem alarming, Apple’s proactive security measures and the inherent design of iOS significantly mitigate the risks.
The occurrence of Safari exploits, although not unheard of, is relatively rare for the average user, thanks in part to Apple’s swift responses to identified vulnerabilities and the deployment of security patches.
Users can further protect themselves by adhering to recommended practices such as installing updates promptly, downloading apps exclusively from the App Store, being cautious of the websites they visit, and employing additional security features like blocking pop-ups and adjusting privacy settings in Safari.
Moreover, the availability of tools like Certo AntiSpy and other vetted security applications offers an added layer of defense against potential threats, ensuring users can maintain their privacy and security while enjoying the benefits of their iPhones.
Ultimately, while no system can be entirely invulnerable, by taking informed precautions and utilizing available security resources, iPhone users can confidently navigate the web through Safari with minimal risk.
Sophia is a Senior Content Manager at Certo Software, showcasing her deep-rooted expertise as an accomplished writer in the tech industry. With a genuine passion for cybersecurity, Sophia is a trusted source of insight and information.

‘Your iPhone has been Hacked, Immediate Action Needed’ Message, How to Fix
Scaring and tricking users into thinking that their devices are somehow compromised is a long-running scam. Apple users have been suffering from this scam, too, even though it is a known fact that security flaws in Apple devices are very rare. A common scam targeted toward iPhone or iPad users is the “your iPhone has been hacked” scam. Sometimes you may get a popup message or be redirected to a screen saying your iPhone is hacked, compromised or accessed, and your actions are being watched without your authorization. The message is designed to scare you. The message also urges you to take immediate action, as you can see below:
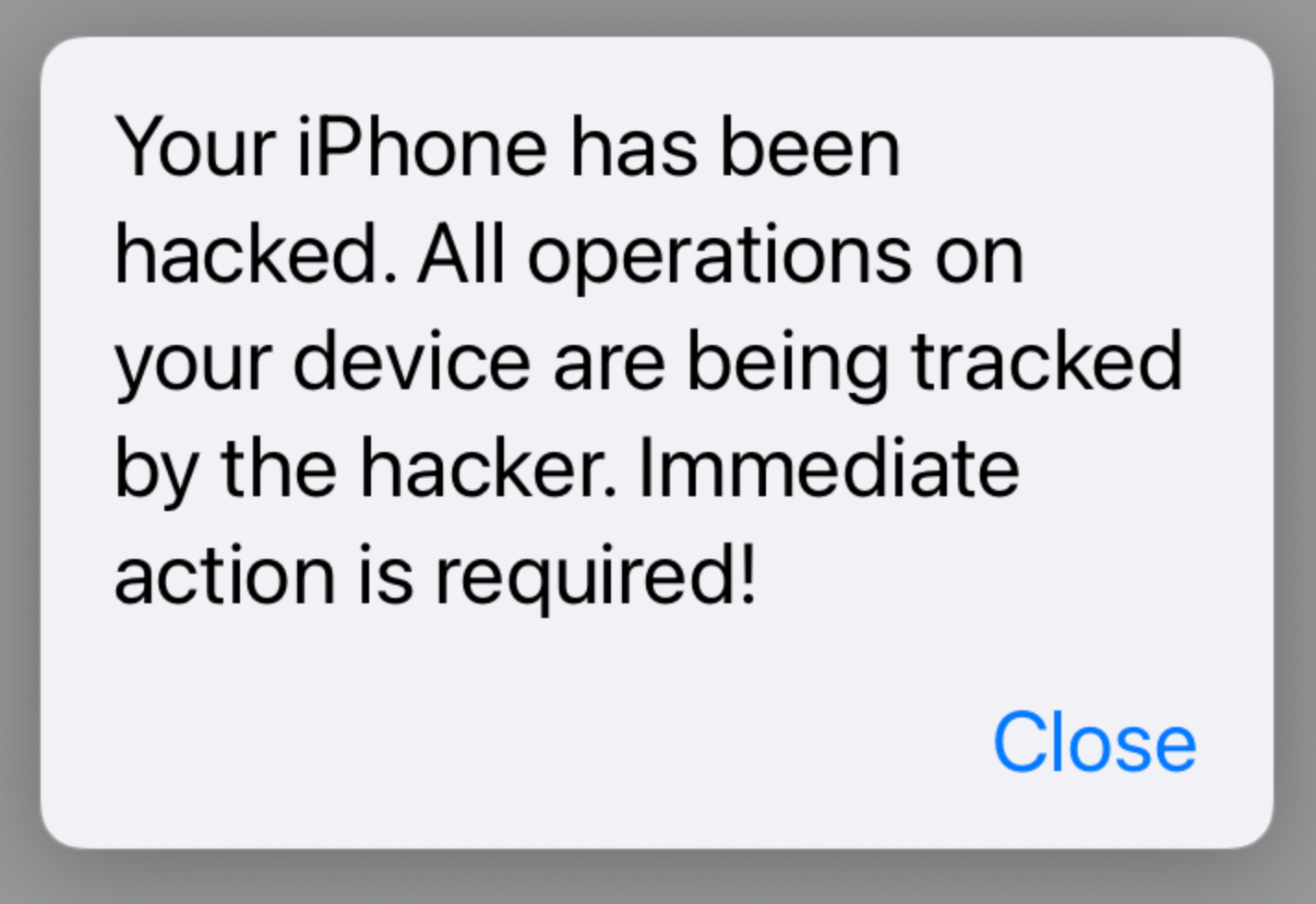
This article explains what you should do if you ever see this message on your iPhone or iPad.
iPhone hacked messages
If you see a message while browsing the Internet in Safari, you can ignore it. I previously wrote about similar scams that you may experience on your iPhone, iPad or Mac. I recommend you check out those articles also:
- iPhone Virus Warning, Is It Real? Fix
- Mac: Your System Is Infected With (3) Viruses, Fix
iOS and iPadOS devices cannot be infected with viruses, malware, spyware or anything similar. This is, of course, true if your device is not jailbroken. I should note that this does not mean that you can’t be the victim of scams. It’s almost always true that these messages are deceitful tactics to trick people into downloading apps. It’s highly likely that you haven’t done anything bad that you should worry about. If you see this message in Safari, here is what you should do:
Do not interact with the notice
- Do not tap anywhere. Usually, these popups have fake buttons. For example, it may say, “Close,” but that may be a button for something else instead of closing it. You may be redirected to another page or the App Store if you tap. If you are redirected to the App Store, do not download and install the app. Simply ignore it. Do not try to exit the popup by tapping the OK or Close buttons on the message.
- If this is an iPhone X and later, swipe up to reveal the most recently used apps, and if you have a Home button, double press the Home button to open the most recently used apps, find Safari and then swipe up on Safari to close.
- Now open Safari again. If the popups come back, again, close Safari. Then go to Settings > Safari and tap Clear History & Website Data . Then open Safari. You won’t see the popup again.
Turn on Safari security settings :
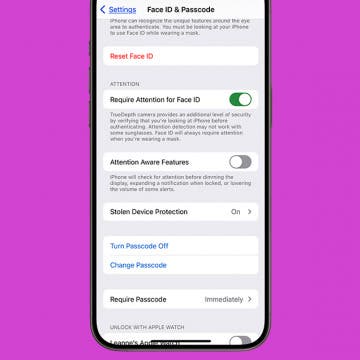
- Go to Settings > Safari and turn on Block Pop-ups . This option is listed under the General section.
- Also, go to Settings > Safari and find the Privacy & Security section and turn on Fraudulent Website Warning and Prevent Cross-Site Tracking .
How to avoid iPhone and iPad hacking
Although these messages are scams, iPhone hacking can happen if you are not careful. iPhone hacking is extremely rare. But your sensitive information can be stolen in various ways. If you want to avoid that, I recommend you follow these ten rules:
- Always keep your iPhone and iPad up to date. Turn on Automatic Updates by going to Settings > General > Software Update > Automatic Updates .
- Always use strong passwords for all the accounts you have. This includes your Apple ID account, your email accounts, your social media accounts, etc. Apple explains what you can do if your Apple ID is compromised .
- Do not share your passwords or Apple IDs.
- Do not jailbreak your iPhone. If you do not know what jailbreaking is, then you are safe. Jailbreaking involves removing software limitations imposed by Apple to allow the installation of unauthorized software.
- Do not download shady apps. Although Apple tries to keep the apps in the App Store closely monitored, the system is not bulletproof.
- Be very careful about phishing attempts . Apple explains how you can recognize phishing scams .
- Turn on Find My, if you have not already, by going to Settings > [your name] > Find My .
- Turn on two-factor authentication . Tap Settings > [your name] > Password & Security and then tap Turn On Two-Factor Authentication .
- Adjust your Auto-Lock timeout. Less is better. Go to Settings > Display & Brightness > Auto-Lock . The least amount of time is 30 seconds, and I recommend this to be set to 30 seconds so that when unattended, your phone cannot be accessed.
- Check your password recommendations, if any, by going to Settings > Passwords > Security Recommendations .
Related articles
- Your Apple ID and Phone Number are Now Being Used, What Does This Mean?
- What Does it Mean when Apple Pay Says ‘Fraud Suspected’?
- Trusted Phone Numbers, Why Are They Important?
Dr. Serhat Kurt worked as a Senior Technology Director specializing in Apple solutions for small and medium-sized educational institutions. He holds a doctoral degree (or doctorate) from the University of Illinois at Urbana / Champaign and a master’s degree from Purdue University. He is a former faculty member. Here is his LinkedIn profile and Google Scholar profile . Email Serhat Kurt .
Similar Posts
Slow mac how to speed up mac: tips and tweaks.
Is your Mac not as fast as it used to be? Do you often see the rainbow-colored circle even when you are doing simple stuff on your computer? Is your Mac noisy indicating your Mac…
iOS: Gmail Won’t Load, Blank Page, Fix
Sometimes, I experience this problem. I use the web version of Gmail. To check my emails, on my iPad or iPhone, I open Safari and go to gmail.com. However, sometimes, Safari displays a…

How to Change the Passcode on iPhone and iPad
The passcode on your iPhone or iPad is the code you enter from the Lock Screen when you can’t open your device using Face ID or Touch ID. You may want to change…

What Is iTunes Match and How Do I Use It?
Did you know that you can sync all of your songs across your devices even if you are not an Apple Music subscriber? This includes all of the songs that you have purchased…
How to Copy Text from a Photo, Image or Live Camera View
Did you know that you can copy and paste text from a photo or screenshot? You can do this on your iPhone, iPad or Mac from the Photos app and in Preview on…
6 FaceTime Calling Issues and Their Fixes
Is FaceTime not working as expected? FaceTime is an incredibly simple application that allows users of iPod Touch, iPhone, and iPad to make real-time video and audio calls with other users who also…
Leave a Reply Cancel reply
Your email address will not be published. Required fields are marked *
Categories:
- Browser Hijacking
- Questions and Answers
- Recover Encrypted Files
- Free Malware Removal Tools
MyAntiSpyware
Your Go-To Destination for Scam Awareness, Malware Removal, Antispyware Downloads, and Expert Guidance
YOUR IPHONE HAS BEEN COMPROMISED scam message (Removal guide)
Myantispyware team May 14, 2022 No Comment
What is YOUR IPHONE HAS BEEN COMPROMISED?
YOUR IPHONE HAS BEEN COMPROMISED is a browser-based scam that disguises itself as an Apple Security page and claims that your iPhone has been compromised due to malware/trojan/virus infection. Scammers use such scams to target victims and force them to install untrusted and even possibly malicious apps. The most common among these apps are PUAs (potentially unwanted applications), adware, browser hijackers and spyware.
Usually, victims end up on “YOUR IPHONE HAS BEEN COMPROMISED” and similar scams by going to a misspelled URL or clicking on a fake link. In addition, they can be redirected to this scam by push notfications, malicious advertisements (malvertising) and Adware.
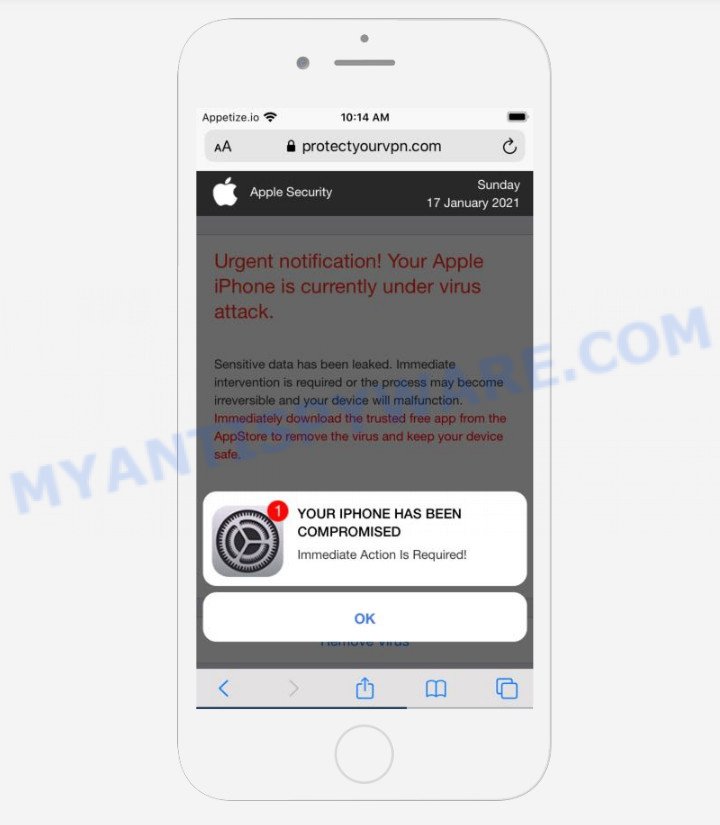
The “YOUR IPHONE HAS BEEN COMPROMISED” message is a SCAM
QUICK LINKS
- What is YOUR IPHONE HAS BEEN COMPROMISED pop-up scam?
The “YOUR IPHONE HAS BEEN COMPROMISED” scam is a widespread form of Internet scam in which scammers instruct victims to install software as a way to prevent data theft, remove malware/trojan/virus, and protect the iPhone from personal information leaks.
This scam is being promoted by sites that are designed to look like a security warning from Apple. It contains the Apple logo and repeated “Apple Security”, “Apple”, “Detected By Apple” phrases, but this does not mean that Apple has anything to do with the creation of these sites, the scammers are simply trying to create the illusion that they are legitimate Apple sites. These sites cannot be trusted and their content should be ignored.
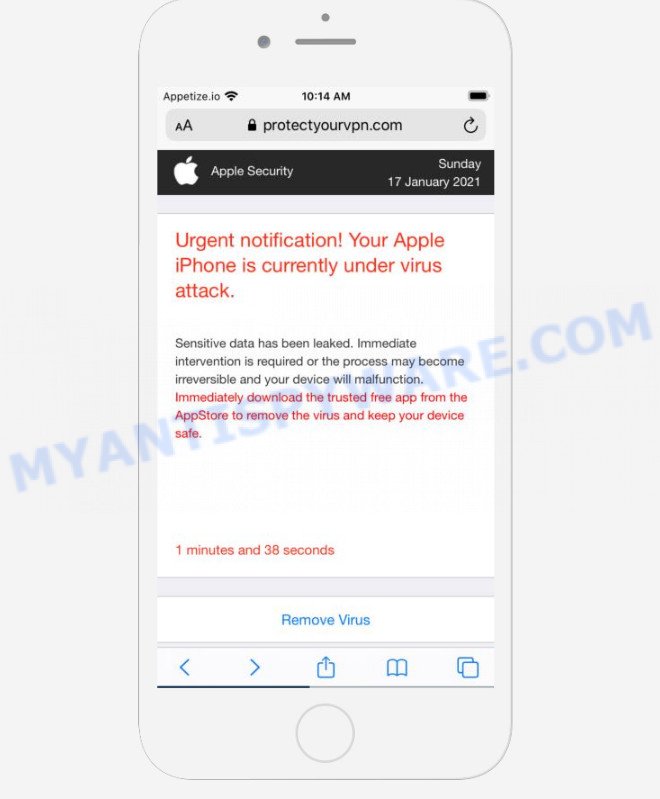
Text presented on the scam:
Apple Security Urgent notification! Your Apple iPhone is currently under virus attack. Sensitive data has been leaked. Immediate intervention is required or the process may become irreversible and your device will malfunction. Immediately download the trusted free app from the AppStore to remove the virus and keep your device safe. 0 minutes and 41 seconds Remove Virus Detected By Apple. YOUR IPHONE HAS BEEN COMPROMISED Immediate Action Is Required! OK
How to protect against the YOUR IPHONE HAS BEEN COMPROMISED scam
To avoid becoming a victim of scammers, it is important to always keep in mind:
- There are no sites that can detect compromised iPhones.
- Never install apps promoted by scam sites, as it can be useless, and besides, it can be dangerous for you and your iPhone.
- Close the scam as soon as it appears on your iPhone screen. Scammers can prevent you from closing it in various ways. In such cases, close your browser using the App Switcher (Open the App Switcher, Tap and hold on the web-browser until the red circles with a minus sign appears. Tap the minus sign on it to Force Quit the web-browser). If the next time you launch the browser, it prompts you to restore the previous session, abandon it, otherwise this scam will reopen on your screen.
Threat Summary
The YOUR IPHONE HAS BEEN COMPROMISED scam isn’t the only one on the Internet that aims to trick users into installing untrusted and malicious apps. We have already reported on other types of scams on several occasions, such as Your connection might not be secure , Iphone Calendar Virus/Spam , SYSTEM NOTIFICATION scam , Your iPhone Has Been Hacked .
Another variant of this scam:

Text presented in this scam message:
Apple Security Urgent action is required! A Trojan virus is detected! The processor is totally overheated, so it can lead to the complete failure of the device and the of all data, including iCloud. Also, all data stored on this device will be available to third parties. Apple Security has urgently selected the required app, which can be downloaded following the link below.It will remove viruses and protect your device in an instant. Remove Virus YOUR IPHONE HAS BEEN COMPROMISED Immediate Action Is Required! OK
A new variant of the YOUR IPHONE HAS BEEN COMPROMISED scam:
Apple Security Warning! Your iPhone was hacked by a virus after visiting an adult website and your screen was recorded! If this problem is not resolved within two minutes, the video recording and all your photos might be leaked. In order to fix the problem you must download trusted VPN app and activate data protection.
Update, March 5, 2021 A new variant of the YOUR IPHONE HAS BEEN COMPROMISED scam (“Your Apple iPhone is severely damaged by 13 viruses”):
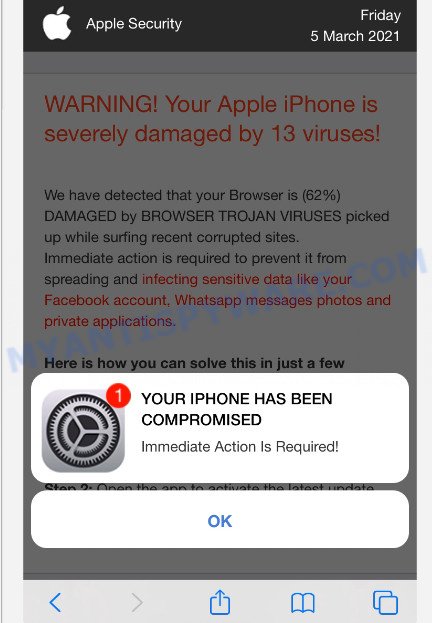
Apple Security WARNING! Your Apple iPhone is severely damaged by 13 viruses! We have detected that your Browser is (62%) DAMAGED by BROWSER TROJAN VIRUSES picked up while surfing recent corrupted sites. Immediate action is required to prevent it from spreading and infecting sensitive data like your Facebook account, Whatsapp messages photos and private applications. Here is how you can solve this in just a few seconds (Step by Step) Step 1: Tap REMOVE VIRUS to install VPN from the App Store. Step 2: Open the app to activate the latest update and remove any older (Infected) versions. Remove Virus Detected By Apple. YOUR IPHONE HAS BEEN COMPROMISED Immediate Action Is Required! OK
Where the YOUR IPHONE HAS BEEN COMPROMISED pop-ups comes from
If your browser redirects to the scam regularly, then it is possible that Adware or PUAs are installed on your iPhone. Adware’s basic purpose is to show advertisements. These advertisements are often displayed as sponsored links, unclosable windows, fake warnings or push notifications. Clicks on the advertisements produce a monetary payoff for the adware creators. Adware can work like Spyware, since it sends confidential data such as searches and trends to advertisers.
Adware spreads bundled with various freeware. This means that you need to be very careful when installing free apps downloaded from the App Store. Be sure to read the Terms of Use and the Software license. Download only reputable applications. NEVER install any unknown and dubious software.
If the YOUR IPHONE HAS BEEN COMPROMISED scam keeps popping up on the device screen and, after closing it, it appears again and again, then try the following simple steps to solve the problem: turn on pop-up blocker; turn on fraudulent website warnings; delete web browsing data. Below we will demonstrate how to do this.
Open the Apple device settings, then scroll down the list of settings to Safari, tap on it.
In the list of settings, find switches “Block Pop-ups” and “Fraudulent Website Warning”, check if they are enabled. If any of the switches are off, then it must be turned on. Having done this, scroll down the settings and tap “Advanced”.
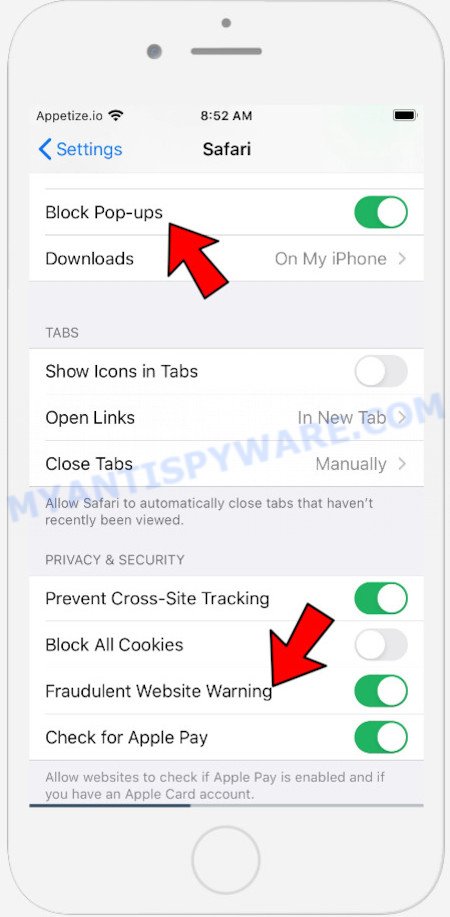
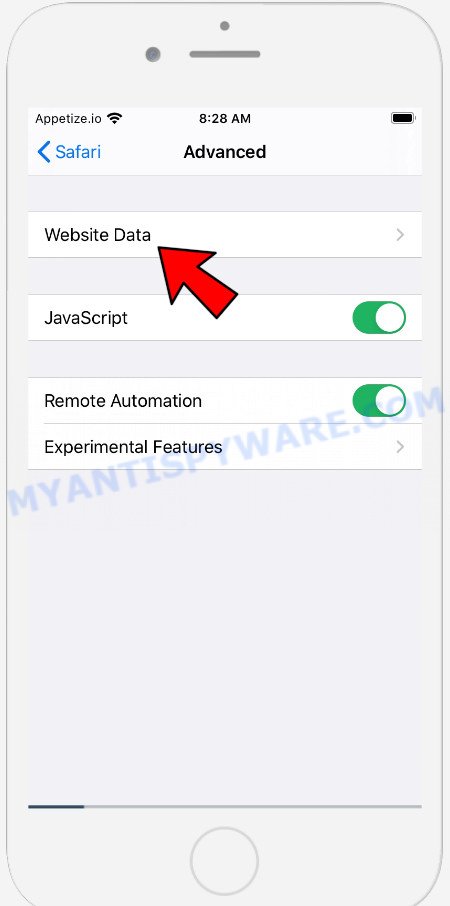
On the Advanced settings screen, tap “Website Data”, scroll down the list of web-domains and tap “Remove All Website Data”.
How to Remove YOUR IPHONE HAS BEEN COMPROMISED scam from Mac (removal instructions)
Fortunately, it is not hard to remove adware software responsible for the YOUR IPHONE HAS BEEN COMPROMISED pop-ups. In the following instructions, we will provide two ways to free your machine of this adware. One is the manual removal solution and the other is automatic removal solution. You can select the method that best fits you. Please follow the removal steps below to remove YOUR IPHONE HAS BEEN COMPROMISED pop ups right now!
To remove YOUR IPHONE HAS BEEN COMPROMISED, use the following steps:
Remove profiles created by adware, check the list of installed apps, remove adware related files and folders, scan your mac with malwarebytes, remove your iphone has been compromised from safari, chrome, firefox, how to stop your iphone has been compromised pop up scam.
Adware and PUAs can install a configuration profile on the Apple Mac system to block changes made to the browser settings. Therefore, you need to open system preferences, find and delete the profile installed by the adware.
In System Preferences, select Profiles. if there is no Profiles in the list of preferences, that means there are no profiles installed on the Mac. If there is Profiles in the list, then click on it, then select a profile related to YOUR IPHONE HAS BEEN COMPROMISED.
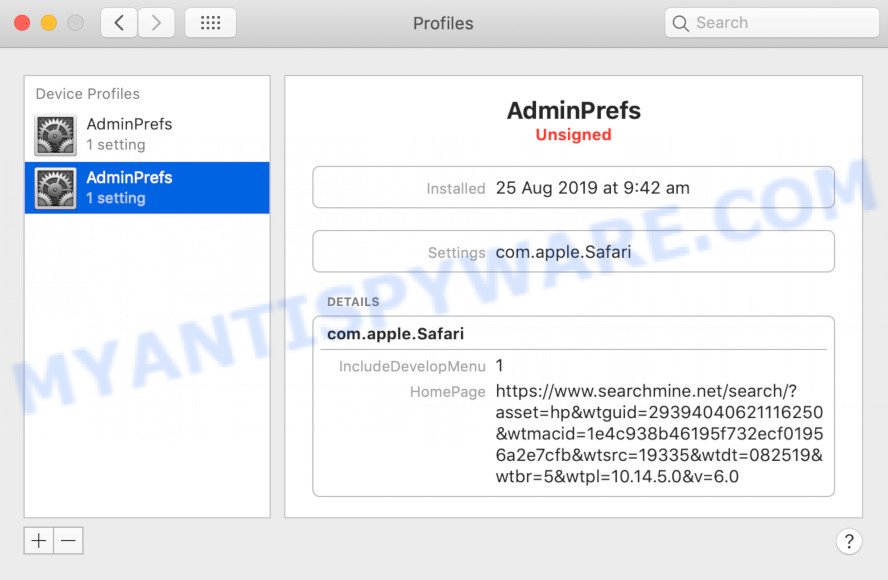
To delete a malicious profile, click on the minus button ( – ) located at the bottom-left of the Profiles screen.

- Open the Finder.
- Click “Applications”.
- It will display a list of all programs installed on the MAC system.
- Scroll through the all list, and remove suspicious and unknown apps. Pay maximum attention to the program you installed last.
- Drag the questionable program from the Applications folder to the Trash.
- Empty Trash.
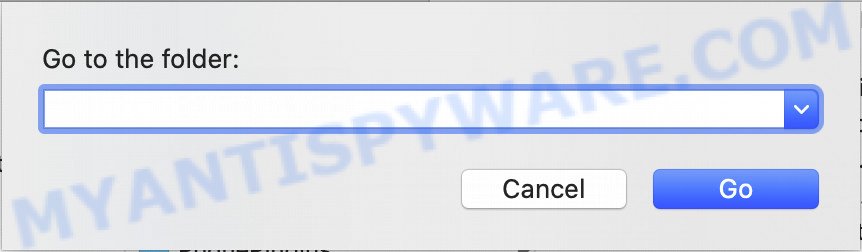
Now you need to try to find adware related files and folders, and then delete them manually. You need to look for these files in certain directories. To quickly open them, we recommend using the “Go to Folder…” command.
Click on the Finder icon. From the menu bar, select Go and click “Go to Folder…”. As a result, a small window opens that allows you to quickly open a specific directory.
Check for adware generated files in the /Library/LaunchAgents folder
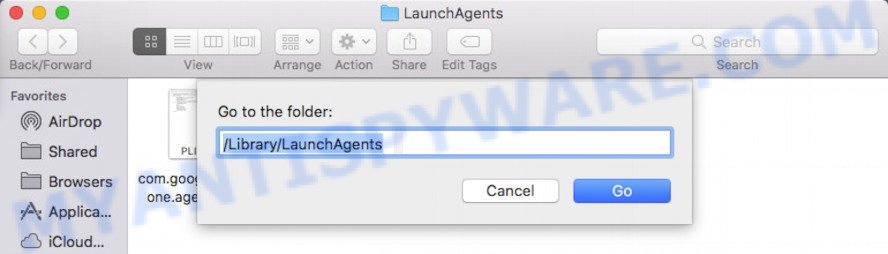
In the “Go to Folder…” window, type the following text and press Go: /Library/LaunchAgents
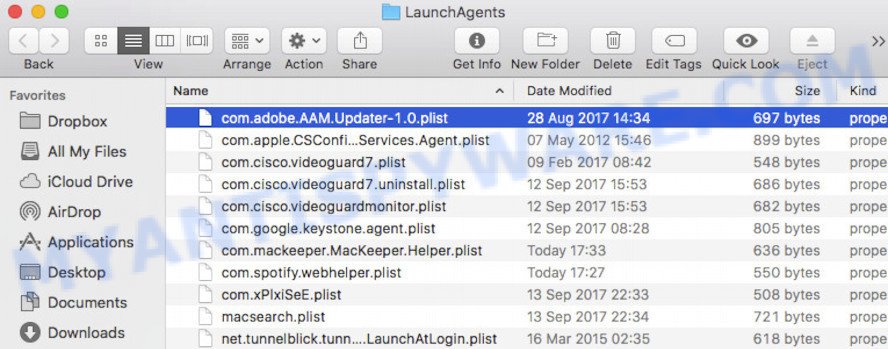
This will open the contents of the “/Library/LaunchAgents” folder. Look carefully at it and pay special attention to recently created files, as well as files that have a suspicious name. Move all suspicious files to the Trash. A few examples of files: installapp.plist, macsearch.plist, search.plist and com.machelper.plist. Most often, adware, PUPs and browser hijackers create several files with similar names.
Check for adware generated files in the /Library/Application Support folder
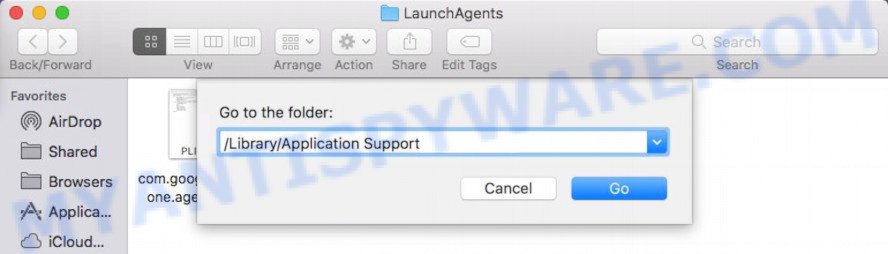
In the “Go to Folder…” window, type the following text and press Go: /Library/Application Support
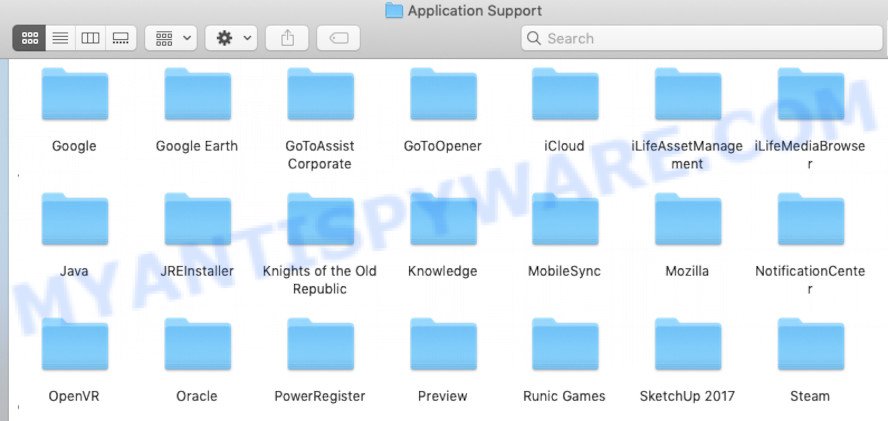
This will open the contents of the “Application Support” folder. Look carefully at its contents, pay special attention to recently added/changed folder. Move all suspicious folders to the Trash.
Check for adware generated files in the “~/Library/LaunchAgents” folder
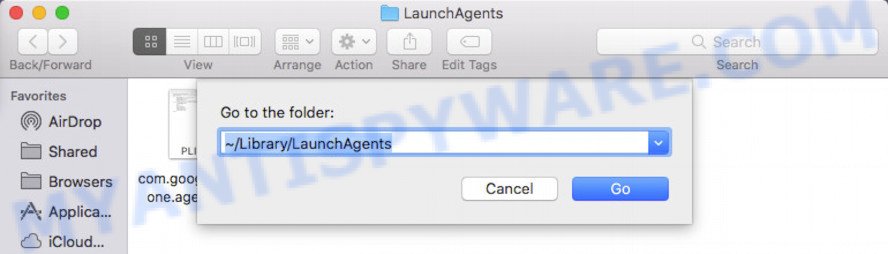
In the “Go to Folder…” window, type the following text and press Go: ~/Library/LaunchAgents
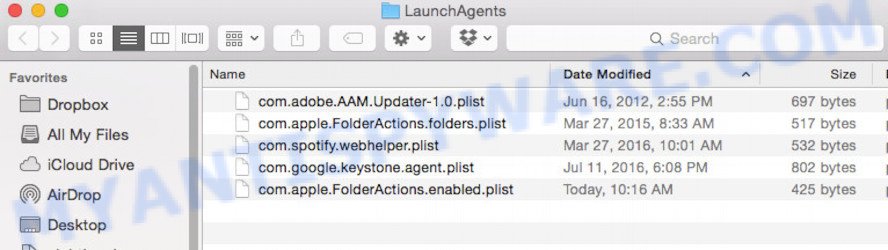
Proceed in the same way as with the “/Library/LaunchAgents” and “/Library/Application Support” folders. Look for suspicious and recently added files. Move all suspicious files to the Trash.
Check for adware generated files in the /Library/LaunchDaemons folder
In the “Go to Folder…” window, type the following text and press Go: /Library/LaunchDaemons
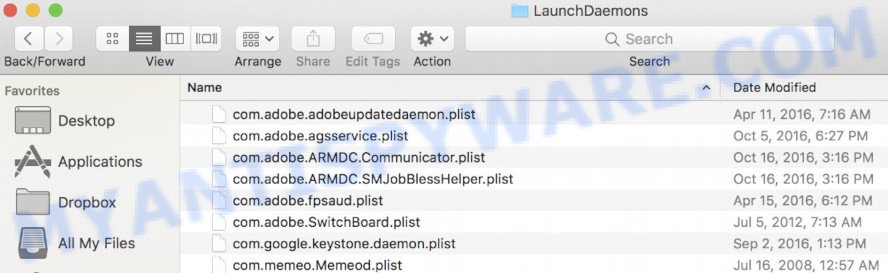
Carefully browse the entire list of files and pay special attention to recently created files, as well as files that have a suspicious name. Move all suspicious files to the Trash. A few examples of files to be deleted: com.macsearch.plist, com.machelper.plist, com.installapp.plist, and com.search.plist. In most cases, adware, browser hijackers and PUPs create several files with similar names.
If you’re still having problems with the YOUR IPHONE HAS BEEN COMPROMISED scam removal or just wish to check your Mac occasionally for adware and other malicious software, then download MalwareBytes AntiMalware (MBAM). It is free for home use, and searches for and removes various unwanted programs that attacks your MAC system or degrades machine performance. MalwareBytes Free can remove adware software, browser hijackers, toolbars and PUPs as well as malware, including ransomware and trojans.
Download MalwareBytes AntiMalware (MBAM) by clicking on the following link.

Once the download is finished, close all programs and windows on your Apple Mac. Run the saved file. Follow the prompts.
The MalwareBytes Anti-Malware (MBAM) will automatically start and you can see its main screen as displayed in the figure below.
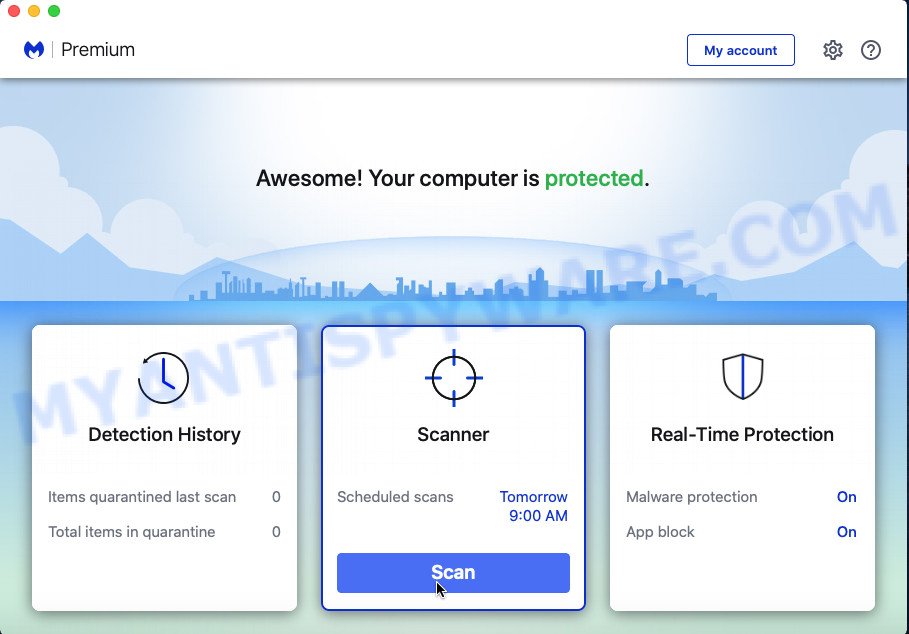
Now press the “Scan” button . MalwareBytes Anti Malware (MBAM) program will scan through the whole MAC OS for the adware responsible for the YOUR IPHONE HAS BEEN COMPROMISED scam. A system scan can take anywhere from 5 to 30 minutes, depending on your MAC. When a malware, adware or PUPs are detected, the count of the security threats will change accordingly.
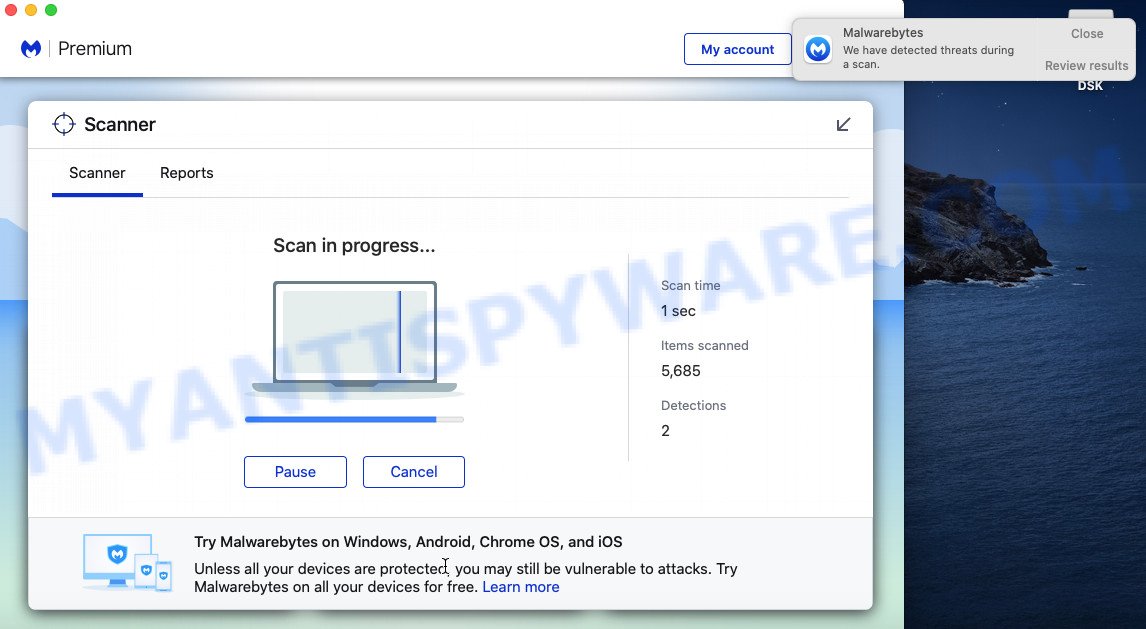
Once the scan get finished, MalwareBytes will show a list of all threats found by the scan. All detected threats will be marked. You can delete them all by simply click the “Quarantine” button. The MalwareBytes Anti-Malware (MBAM) will start to delete adware that causes the YOUR IPHONE HAS BEEN COMPROMISED pop ups in your web-browser.
If you have ‘YOUR IPHONE HAS BEEN COMPROMISED pop-up scam’ removal problem, then remove unwanted add-ons can help you. In the steps below we’ll show you the way to remove harmful plugins without reinstall. This will also allow to delete YOUR IPHONE HAS BEEN COMPROMISED popups from your web browser.
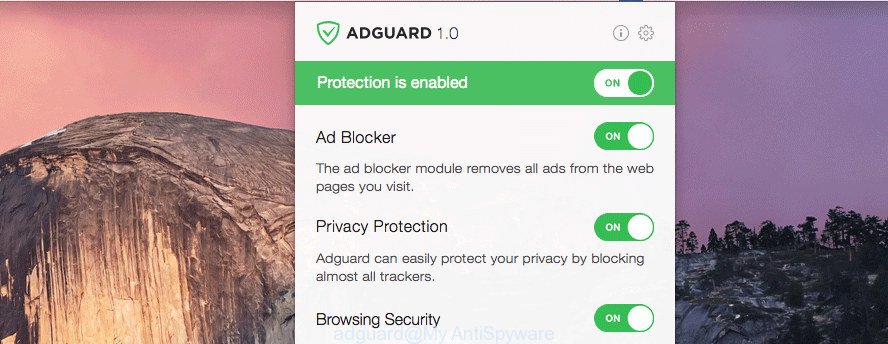
Click the link below to download the latest version of AdGuard for Mac.
After the downloading process is finished, run the downloaded file. The “Setup Wizard” window will show up on the computer screen.
Follow the prompts. AdGuard will then be installed. A window will show up asking you to confirm that you want to see a quick tutorial. Click “Skip” button to close the window and use the default settings, or press “Get Started” to see an quick tutorial that will allow you get to know AdGuard better.
Each time, when you run your machine, AdGuard will run automatically and stop intrusive pop-up advertisements, block YOUR IPHONE HAS BEEN COMPROMISED scam, as well as other malicious or misleading websites.
Finish words
Once you’ve finished the instructions shown above, your Apple device should be free from adware responsible for the YOUR IPHONE HAS BEEN COMPROMISED scam and other malware. The Firefox, Safari and Google Chrome will no longer redirect you to various scam web-pages similar to YOUR IPHONE HAS BEEN COMPROMISED. Unfortunately, if the step-by-step instructions does not help you, then you have caught a new adware, and then the best way – ask for help here .
Author: Myantispyware team
Myantispyware is an information security website created in 2004. Our content is written in collaboration with Cyber Security specialists, IT experts, under the direction of Patrik Holder and Valeri Tchmych, founders of Myantispyware.com.
Leave a Reply Cancel reply
Remove MagnaEngine browser hijacker: Chrome, Edge, Firefox 💡
‘I was planning to say hello’ Email, Scam or Real, Should you be worried?
CELEMEX.com Bitcoin Scam: Promo Codes as a Trap
Remove Boyu.com.tr Redirect: Chrome, Edge, Firefox

Vonef.com Review: Decoding the Bitcoin Promo Code Scam
Useful guides.

Best Free Malware Removal Tools 2024

How to reset Mozilla Firefox (Updated Apr. 2018)

How to reset Google Chrome settings to default

How to remove browser hijacker virus (Chrome, Firefox, IE, Edge)

How to remove Adware from Windows 10 (Virus removal guide)
Recent posts.
1LzA9kzQkGDTYSfbbLE8gK5RAJ5ke32ntC Bitcoin Email Scam
How to remove Prizepagoda.com pop-ups (Virus removal guide)

How to uninstall HotComplete app/extension from Mac (Virus removal guide)
How to get rid of M.gsearch.co redirect from Chrome, Firefox, IE, Edge
How to remove Mycomputerads.com pop-ups (Virus removal guide)
More From Forbes
New ‘dangerous’ iphone spyware attack warning issued to ios users.
- Share to Facebook
- Share to Twitter
- Share to Linkedin
Apple iPhone users have been issued a new warning after security researchers found a prolific and dangerous spyware campaign has returned. Researchers from security outfit and former smartphone giant BlackBerry discovered a spyware campaign dubbed “LightSpy” targeting iPhone users in Southern Asia and “probably India.”
It comes after Apple issued a spyware warning last week, with iPhone users in 92 countries receiving alerts to indicate their device may have been compromised. The LightSpy campaign ties in with this warning, with iPhones in India being targeted, submissions from malware analysis website VirusTotal show.
Researchers from BlackBerry discovered a spyware campaign dubbed “LightSpy” targeting iPhone users ... [+] in Southern Asia and “probably India.”
The location of the iPhone spyware campaign potentially indicates “a renewed focus on political targets and tensions in the region,” according to the blog posted by the BlackBerry researchers.
LightSpy is “particularly dangerous” because it can allow an attacker to locate their target with “near-perfect accuracy,” the BlackBerry researchers said.
What is LightSpy iPhone spyware?
It’s not the first time LightSpy has been discovered. The iPhone spyware—described as a “sophisticated iOS implant,” was first reported in 2020 amid rising political tensions in Hong Kong.
Rudy Giuliani And Mark Meadows Indicted In Arizona Fake Electors Case
Tupac shakur s estate challenges drake over ai vocals in kendrick lamar diss song, apple iphone 16 unique all new design promised in new report.
The latest iteration of LightSpy has more extensive spying features than the first, the researchers said.
“Specifically, it is a fully-featured modular surveillance toolset that primarily focuses on exfiltrating victims’ private information, including hyper-specific location data and sound recording during voice over IP (VOIP) calls.”
LightSpy possesses modules designed to exfiltrate iPhone device information and saved files, including data from popular messenger applications such as QQ, WeChat, and Telegram. It also has a plugin capable of crawling the payment history of the victim from WeChat Pay (Weixin Pay in China).
The iPhone spyware can access a user’s contacts, SMS messages, phone call history, GPS location, connected WiFi history and the browser history of Safari and Chrome. “This comprehensive set of features can turn a user’s infected phone into a potent spying device,” the researchers warned.
Evidence such as code comments and error messages strongly suggest the attackers behind LightSpy are native Chinese speakers, raising concerns about potential state-sponsored activity, BlackBerry’s researchers said.
New iPhone Spyware Warning—The Risk
It’s a scary warning and something that all iPhone users should be careful of. However, spyware tends to target a specific subset of users.
“Though typically deployed against a very small percentage of individuals—most usually journalists, activists, politicians and diplomats—hyper-focused spyware attacks are an ongoing and global threat,” BlackBerry researchers warned.
Any iPhone users who fit into this category can use Apple’s super-secure anti-spyware tool Lockdown Mode to help prevent an attack.
Spyware itself is very hard to detect, but signs your iPhone could be compromised include a very hot or a slowed device. It’s worth noting that if you switch off your iPhone, it can sometimes disrupt spyware temporarily.
In the case of LightSpy, BlackBerry reckons initial infection likely occurs through compromised news websites carrying stories related to Hong Kong. Therefore, be very careful of the sites you visit and links you click on your iPhone. Only download from sources you trust.
The most important thing here is to ensure you always update your iPhone to the latest software, in this case iOS 17.4.1 , by visiting Settings > General > Software Update and downloading and installing it now.

- Editorial Standards
- Reprints & Permissions
If you think your Apple ID has been compromised
If you're concerned that an unauthorized person might have access to your Apple ID, these steps can help you regain control of your account.
Signs that your Apple ID has been compromised
Apple notified you (notification or email) about accounty activity that you don't recognize (for example, if your Apple ID was used to sign in to a device that you don't recognize or your password was changed but you didn't change it).
You notice unusual activity like messages that you didn't send, deleted items that you didn’t delete, or purchase activity that you don't recognize.
Your password no longer works, you don't recognize some or all of your account details, or your device was locked or placed in Lost Mode by someone other than you.
Learn how to recognize and avoid phishing scams
Learn what to do if you see an unfamiliar iTunes Store or App Store charge
Gain control of your Apple ID
Change your Apple ID password
If your Apple ID password has been changed by someone else, reset your password .
Go to appleid.apple.com to update any of personal or security information that isn't correct or that you don't recognize.
Check with your email address* provider to make sure that you control every email address associated with your Apple ID. If you don't control an email address, work with your email provider to regain control or use a different email address.
* In China mainland and India, you can use your phone number as your Apple ID
If you can't reset your Apple ID password or sign in
If you can't reset your Apple ID password or sign in to appleid.apple.com, go to iforgot.apple.com to start account recovery and regain access after an account recovery waiting period.
Learn more about account recovery
Secure your Apple ID
After you regain control of your Apple ID, follow these instructions to make sure that you control all of the Apple IDs signed in to your devices and that your Apple ID is secure.
Know which Apple ID is signed in to your device
To make sure that you're signed in to Apple IDs that only you control or trust, check the settings on each of your devices.
Open the Settings app on your iPhone, iPad, iPod touch, or Apple Watch, or System Settings (or System Preferences) on your Mac.
You should see your name. Tap your name and verify the email address associated with your Apple ID.
On each of your devices, check the settings for services that you're signed in to with your Apple ID (including FaceTime, Messages, the iTunes Store and the App Store, Internet Accounts, Mail, and Calendar).
Check iCloud for Windows, your HomePod (using the Home app on your iPhone or iPad), and your Apple TV (for iCloud Photos or Home Sharing).
Make sure that your Apple ID is secure
If you haven't already, set up two-factor authentication for your Apple ID . This additional security feature is designed to prevent someone else from accessing your account, even if they know your password.
You should be the only person who knows your password and can sign in with your Apple ID.
If someone you don't know or don't trust can sign in with your Apple ID, your account is not secure.
To help keep your Apple ID secure, you should also keep your device secure and protect your device with a passcode. If someone else has your trusted device and knows your passcode, they can reset your Apple ID passcode. Learn how to secure your device if it's lost or stolen .
Learn more about how to keep your Apple ID secure

Related topics
Contact Apple Support
Need more help? Save time by starting your support request online and we'll connect you to an expert.
Looks like no one’s replied in a while. To start the conversation again, simply ask a new question.
Your iPhone Has Been Hacked Pop Up
I was taking an online quiz when I got the pop up notification that “My iPhone has been hacked. All actions are being tracked by a hacker. Take action immediately!”. Instead of pressing the close option at the bottom of the pop up I exited out of the tab immediately. I researched and found out it’s a scam but since I didn’t open anything I don’t know if my phone was effected in any way. I went into my settings and changed my safari settings to block pop ups, turn on fraudulent website warning, and clear my website data. I’m about to complete a software update, but I’m unsure if my phone is safe or not. Please help!
Posted on Aug 6, 2021 10:41 PM
Posted on Aug 7, 2021 5:31 PM
Hello Dogs117!
Looks like you are having some trouble with Safari popups on your iPhone. We wan to help! That notification is just a phishing attempt and is safe to ignore. This article has more information: About pop-up ads and windows in Safari .
Similar questions
- Pop-up on my iPhone says I've been hacked I got a pop-up when I was on a website on my iPhone and it said that my phone has been hacked and is being spied upon. I did not press anything on that page, but I did turn my phone off immediately and then contact you [Re-Titled by Moderator] 7577 2
- Pop up saying iPhone was hacked I am thinking this is a scam but twice I have been playing a game on my phone. All of the sudden my phone goes into Safari. A pop up comes up from etrafficmedia.com. It reads Your iPhone has been hacked. All operations on your iPhone are being tracked by the hacker. Immediate action is required! the only option is to close and it pops up saying to click to fix and then a count down timer. I just closed the window, deleted the app I was on and cleared my browser history. Is this a scam? 4591 4
- Pop up on my screen said my iPhone has been hacked while surfing the Internet, a pop up appeared on my screen saying my phone has been hacked. I closed out of the browser right away. How do I know if this is legit? [Re-Titled by Moderator] 8970 2
Loading page content
Page content loaded
Aug 7, 2021 5:31 PM in response to Dogs117
Three Ways to Fix a Safari Browser Hijack in iOS 11
There’s a particularly nefarious form of hijackware that can take over Safari in iOS. Fortunately, there are three fairly easy ways to solve an iOS browser hijack (also called a Safari hijack): clearing your cache, disabling JavaScript, and using an external link to force open a new window or tab. I’ll explain each of these methods below.
You can skip to the instructions if you don’t want the description first.
Safari Hijack in iOS
A browser hijack, or safari hijack, is when a malicious webpage—or more likely, a malicious ad on an otherwise legitimate webpage—takes over your browser. There are a few different versions of this. One variant puts a dialog box on your screen asking you to call a phone number, like in the screenshot below.
WARNING: NEVER CALL A PHONE NUMBER LIKE THIS—IT’S A SCAM BY BOTTOM FEEDING SCUMBAGS TRYING TO TRICK YOU INTO GIVING THEM YOUR CREDIT CARD INFO!
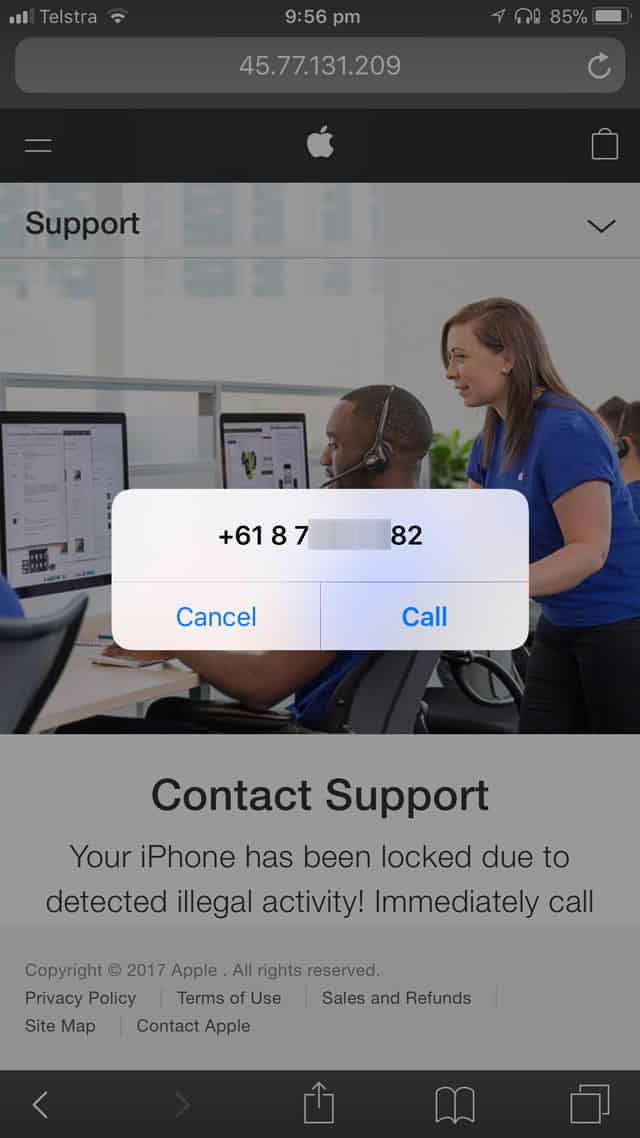
The way this one worked was that you couldn’t cancel or otherwise dismiss the dialog box. And see how it looks all official, like it’s something form Apple? It isn’t. Instead, it’s JavaScript shenanigans whose only goal is to get you to call the thieves and hand over personal data, credit card info, and sometimes remote access to your device.
So, as the warning says, don’t fall for this, never call a number like that, and use the methods below to get around a safari hijack like this if you stumble into one.
Browser Hijack Variant
Another variation is the one I encountered below. In this version, a maliciously—or maybe just poorly—coded ad didn’t hijack my entire browser. Instead, it hijacked the webpage I was trying to visit. No matter what I did, I was rerouted to some spammy BS site when I opened Safari.
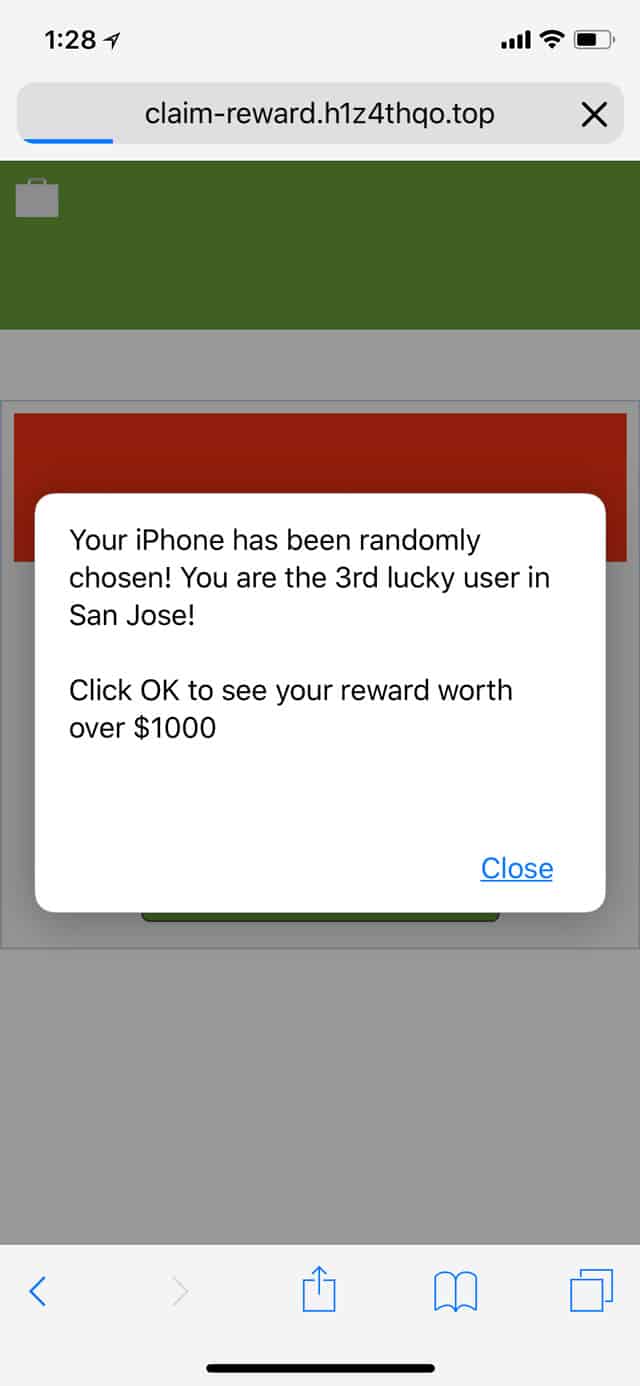
These hijacks usually aren’t the fault of the site operator, and sometimes not even the ad network they’re on. Spammers and thieves are engaged in an unrelenting effort to get their maliciously crafted ads onto ad networks, especially the automated ones. While most of those networks remove the malware ads (eventually), the bad guys are always trying to get new ones in.
Next: How to Fix a Safari Hijack in iOS 11
3 thoughts on “ Three Ways to Fix a Safari Browser Hijack in iOS 11 ”
This didn’t help me at all, on my iPad. Still getting hijacked with regularity. What I mean is, even with JavaScript disabled, I get hijacked, bu at least can go back to the page. Problem is the sites where this is happening are useless without JavaScript. Amazed the hell out of me that I cannot blacklist sites in safari, or even chrome on iPad, I would need to use a wildcard as they change it but my tormenter begins with eu.*.out or something like that. Wild card in place of the field that changes each time. This is making browsing unusuable. One of the sites is huffingtonpost and they are basically unreachable anyway.
Sorry but this is just the ad network being weaponized. I will make a few repeat visits to sites where this happens and notify the site, but if it persists more than a couple of visits, that’s it, I’m blacklisting you. In general this is among the reasons “we can’t have nice things”, but that is the world we live in. If ad networks can’t fix this problem quickly, it will be the well-deserved end of them.
This happens to me at a few website that I regulalry visit. I will report to the webmaster who will investigate and 86 the ad, but a few days later the slimeball is at it again.
Maybe the answer would be for website to not allow advertisers to use javascript in the ads, just a simple link. It would probably speed up the page load.
Leave a Reply Cancel reply
You must be logged in to post a comment.
This site uses Akismet to reduce spam. Learn how your comment data is processed .
- Bryan Chaffin
Dangerous LightSpy iPhone spyware can steal your files, location data and messages — how to stay safe
Hackers are coming up with new ways to spy on iPhones

iPhone users are once again being targeted by dangerous spyware capable of tracking their location as well as stealing their contacts, messages and even data from a number of popular apps.
Apple recently sent out a warning to iPhone users in 92 different countries about the threat posed by spyware. Now though, we have more details on a new version of the LightSpy spyware which is currently being used to target iPhones in Southeast Asia and India.
While this latest campaign hasn’t been observed in the U.S. or the U.K. yet, it could easily be modified to target the best iPhones in Western countries too. Here’s everything you need to know about the LightSpy spyware, including some tips on how you can keep your iPhone safe from hackers.
Stealing browser and app data

First discovered back in 2020 by Trend Micro and Kaspersky, LightSpy is an iOS backdoor that is often distributed to unsuspecting iPhone users through compromised news sites according to The Hacker News .
Then in 2023, the cybersecurity firm ThreatFabric noticed that it shares some of the same infrastructure and functionality with the DragonEgg Android spyware developed by APT41, which is a state-sponsored hacker group from China.
While we’re not entirely sure how LightSpy is being distributed in this latest campaign, in the past, it’s been spread through news sites that have been compromised by hackers. A LightSpy infection begins with a loader that contains the main components of the spyware, after which a number of plugins are downloaded from a remote server that allow it to steal all sorts of sensitive data.
While this spyware could initially steal an iPhone user’s contacts and messages, determine their precise location and extract audio recordings during VoIP calls, a new version was recently discovered by BlackBerry with upgraded capabilities. LightSpy can now steal files from a vulnerable iPhone as well as data from a number of popular apps including Telegram, QQ and WeChat. However, the spyware is also able to steal iCloud keychain data as well as a victim’s browsing history from both Safari and Google Chrome .
Sign up to get the BEST of Tom’s Guide direct to your inbox.
Upgrade your life with a daily dose of the biggest tech news, lifestyle hacks and our curated analysis. Be the first to know about cutting-edge gadgets and the hottest deals.
In their report on the matter, BlackBerry’s security researchers also revealed that the spyware can gather a list of connected Wi-Fi networks and details about the apps installed on your iPhone in addition to taking pictures using the device’s camera and recording audio through its microphone. To make matters worse, LightSpy can execute shell commands from a remote service, which could likely allow it to take complete control over infected iPhones.
How to keep your iPhone safe from hackers

Although spyware remains a very serious threat due to just how much personal and financial data we store on our phones, attacks like the one described above are both difficult and costly to pull off. As such, hackers and other cybercriminals mainly use spyware like LightSpy to go after high-profile targets such as politicians, CEOs and political dissidents.
This doesn’t mean that you should ignore the threat posed by spyware though. In a blog post , BlackBerry recommends that iPhone users who are worried about spyware enable Apple’s Lockdown Mode for additional protection.
At the same time, you should be using the best encrypted messaging apps to communicate with others since they employ end-to-end encryption to prevent prying eyes from gaining access to your conversations. Apple’s iMessage uses this kind of encryption but only between other iPhone users, which is why you may want to use Signal or a similar encrypted messaging app when communicating with Android users.
Like with malware and other cyber threats, the most important thing you can do to stay safe is to keep your devices updated, enable two-factor authentication (2FA) whenever possible and use strong, complex passwords for all of your accounts. The best password managers can help with the last part since they all contain password generators which can create strong and unique passwords as well as securely store all of your existing passwords. You also want to be careful when downloading new apps or files and when visiting new websites since the hackers behind this campaign used compromised sites to distribute the LightSpy spyware.
As one of the best phones for years now, the iPhone will likely always remain a target for hackers. However, by exercising caution online and updating your phone regularly, you should be able to avoid falling victim to hackers.
More from Tom's Guide
- Macs under threat from info-stealing malware spread through bad ads
- Worried about spyware on your iPhone? iShutdown can help
- This Android banking trojan now lets hackers remotely control your phone

Anthony Spadafora is the security and networking editor at Tom’s Guide where he covers everything from data breaches and ransomware gangs to password managers and the best way to cover your whole home or business with Wi-Fi. Before joining the team, he wrote for ITProPortal while living in Korea and later for TechRadar Pro after moving back to the US. Based in Houston, Texas, when he’s not writing Anthony can be found tinkering with PCs and game consoles, managing cables and upgrading his smart home.
Forget the iPad — it's the iPhone 16 Pro that needs Apple Pencil 3 support
Google Maps on iPhone may finally get this useful navigation feature
What is the Casper One mattress and should you buy it in Memorial Day sales?
Most Popular
- 2 Do mattress toppers help with back pain or make it worse? Experts respond
- 3 After TikTok, DJI drone ban could be next for US lawmakers
- 4 Google Pixel 8a could get seven years of security updates — here's why
- 5 Should you buy a mattress from Amazon, Walmart or Costco? Pros and cons

IMAGES
VIDEO
COMMENTS
Giulio. Being aware that an iPhone, unless jailbroken, cannot be hacked remotely if you ignore and DO NOT respond/click on any link that it might contain, see this support article:--> Recognize and avoid phishing messages, phony support calls, and other scams - Apple Support. To feel more comfortable, in addition to deleting the history and ...
Apple compares passwords that are in the Keychain app on your phone with that list, and tells you about the ones that appear both in Keychain and the list maintained by security teams. To see the list Apple has compiled go to Settings/Passwords and tap on Security Recommendations. If you have received a message telling you that your passwords ...
To close apps on iPhones earlier than iPhone 8, double-click the circular Home button. This will open up the app switcher. From there, swipe up on the app to close it out. For iPhones without a Home button (X, XR, XS, XS Max), swipe up from the bottom of the screen to the center of the screen. Hold your finger in the center of the screen until ...
Experian: 1-888-397-3742 or online. TransUnion: 1-888-909-8872 or online. 10. Factory reset your iPhone. Factory resetting your phone is a last resort, but if you've tried the other methods listed above and your phone is still showing signs of being hacked, this is a surefire way to get a hacker out of your phone.
Published on: September 23, 2022. You're browsing on your iPhone when a scary pop-up appears warning "Your iPhone Has Been Hacked.". It claims malicious spyware was detected on your iOS device. The message demands you call a support number immediately to remove the hackers. This dire alert seems concerning, but hold up - it's actually ...
If you believe that your Apple ID has been compromised, ... Learn how to safely open software on your Mac or remove unwanted configuration profiles from your iPhone, iPad, or iPod touch. 1. To report an SMS text message, take a screenshot of the message and send it via email. ... If you can't see the URL in the status bar in Safari, choose View ...
Tap Clear History and Website Data. While in Safari settings, toggle on Fraudulent Website Warning. Toggle on Block Pop-ups as well. Tap on Settings in the upper-left corner. Toggle Airplane Mode back off. Now you can open Safari again; at this point, Apple virus scams shouldn't be appearing anymore.
Apr 28, 2021 11:43 AM in response to kyliea1007. Safari itself did not say your iPhone was hacked. A fraudulent website wants you to think your iPhone has been hacked. If an iPhone has not been jailbroken, there is no known way for it to get malware. Any popup, message, website, or phone call saying your iPhone has been infected or compromised ...
To make sure that you're signed in to Apple IDs that only you control or trust, check the settings on each of your devices. Open the Settings app on your iPhone, iPad, iPod touch, or Apple Watch, or System Settings (or System Preferences) on your Mac. You should see your name. Tap your name and verify the email address associated with your ...
19 Sep 2022 • 7 min. read. Let's be clear: if your iPhone or iPad is connected to the internet, there's a risk it might get hacked. Sure, statistics seem to support the idea that your iOS ...
Step 2: Examine Battery Usage. Check your iPhone's battery usage to see if there are any apps running in the background that you're not aware of. A sudden drop in battery life could be a sign of malicious software running on your iPhone. Go to 'Settings' > 'Battery' and look for any apps that are using a disproportionate amount of ...
Keeping your iPhone up-to-date via Settings > General > Software Update is one of the best ways to protect your iPhone.; Never share your Apple ID password or PIN for your iPhone. Avoid malicious ...
Media & Purchases Compromised Find My Compromised. iPhone This iPhone. Repair now. The "Your Device Apple iPhone Has Been Hacked" pop-up has nothing to do with Apple and anything it states is just false. If you have been redirected to the "Your Device Apple iPhone Has Been Hacked" ads, we recommend closing the page and do not enter any ...
A spoofed warning that says, "Your iPhone Has Been Hacked" is yet another common type of the fraudulent Safari alert. It relies on a similar logic, attempting to hoodwink the would-be victim into disclosing account credentials or dialing a phone number to contact a pseudo-technician who will try to wheedle out personally identifiable ...
Chrome: Open Chrome, tap the three dots at the bottom-right, select History, and then tap Clear Browsing Data. Select All Time as the time range and tap Clear Browsing Data at the bottom. 5. Update your iPhone. If a hacker has gained access to your iPhone, it could be due to a security hole in iOS. [3]
To get rid of this nonsense, you'll want to attempt to follow the steps outlined here: Safari Pop-up scam fix: • Swipe up to access your quick settings, or just go to Settings. • Activate ...
Remove "Your iPhone has been hacked" in Google Chrome. Open Chrome, click the Customize and control Google Chrome (⁝) icon in the top right-hand part of the window, and select Settings in the drop-down. When on the Settings pane, select Advanced. Scroll down to the Reset settings section. Confirm the Chrome reset on a dialog that will pop up.
Some Safari exploits may try to install spyware on your device, providing a hacker with complete remote access to your device. If you suspect your iPhone has been hacked, you can use an anti-spyware tool like Certo AntiSpy to perform a deep scan of your phone. This can help to detect hidden spyware and remove threats from your device.
A common scam targeted toward iPhone or iPad users is the "your iPhone has been hacked" scam. Sometimes you may get a popup message or be redirected to a screen saying your iPhone is hacked, compromised or accessed, and your actions are being watched without your authorization. ... If you see a message while browsing the Internet in Safari ...
Go to Settings > Passwords > Security Recommendations. If an account has a weak or compromised password, a message explains the problem. Tap an account. Tap the Password field, then tap Copy Password, so you can paste it where it's requested—for example, when you create a new password and you're asked to enter your old password.
The popup may not have been legit (I can't find how Apple notifies users of password issues when using Safari) and you could have been taken for a very bad ride. Now, independent of the popup, you saw that you have passwords issues: you know what to do and, most importantly, safely, because you are not clicking on a dubious link.
Remove YOUR IPHONE HAS BEEN COMPROMISED from Safari, Chrome, Firefox; How to stop YOUR IPHONE HAS BEEN COMPROMISED pop up scam; Remove profiles created by adware. Adware and PUAs can install a configuration profile on the Apple Mac system to block changes made to the browser settings. Therefore, you need to open system preferences, find and ...
It comes after Apple issued a spyware warning last week, with iPhone users in 92 countries receiving alerts to indicate their device may have been compromised. The LightSpy campaign ties in with ...
To make sure that you're signed in to Apple IDs that only you control or trust, check the settings on each of your devices. Open the Settings app on your iPhone, iPad, iPod touch, or Apple Watch, or System Settings (or System Preferences) on your Mac. You should see your name. Tap your name and verify the email address associated with your ...
Pop up saying iPhone was hacked I am thinking this is a scam but twice I have been playing a game on my phone. All of the sudden my phone goes into Safari. A pop up comes up from etrafficmedia.com. It reads Your iPhone has been hacked. All operations on your iPhone are being tracked by the hacker.
Amazed the hell out of me that I cannot blacklist sites in safari, or even chrome on iPad, I would need to use a wildcard as they change it but my tormenter begins with eu.*.out or something like ...
iPhone users are once again being targeted by dangerous spyware capable of tracking their location as well as stealing their contacts, messages and even data from a number of popular apps. Apple ...